888 RAT- The Payload Creator

If you want to learn about 888 RAT then you are at the right place in this article you will learn about 888 rat and their use. In this article, you get a demo practical in LAN to make you…
An act of compromising networks and data through unauthorized access to an account or system

If you want to learn about 888 RAT then you are at the right place in this article you will learn about 888 rat and their use. In this article, you get a demo practical in LAN to make you…
A vulnerability in Linux, nicknamed “Dirty Pipe”, which allows an unprivileged user to overwrite data in read-only files. This can lead to privilege escalation which result inject code into the root processor. This Vulnerability was found by Max Kellerman of…
Zero Trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and continuously validated for security configuration and posture before being granted or keeping access to applications and data. Zero Trust assumes…


If you have searched about keyloggers and want to learn about them then you are at the right place in this article, you will know about keyloggers and know the use of a Software keylogger with a demo practical using…
Cyberterrorism is defined as the strategically premeditated attack over the internet that mainly focuses over political disarray or physical harm of the state at a huge level. The U.S. Federal Bureau of Investigation (FBI) defines cyberterrorism as any “premeditated, politically…

Panasonic, The Japanese tech company has confirmed data breach after the hackers accessed the personal information of the job candidates and interns. Company said that it network was illegally accessed by a third party on November 11. NHK (Japanese publication)…

A vulnerability in the open source Log4J logging service used by developers to monitor their Java applications first came to light, leaving enterprises scrambling to patch affected systems. Since then, the vulnerability dubbed CVE-2021-44228 has been highly exploited in the wild with…
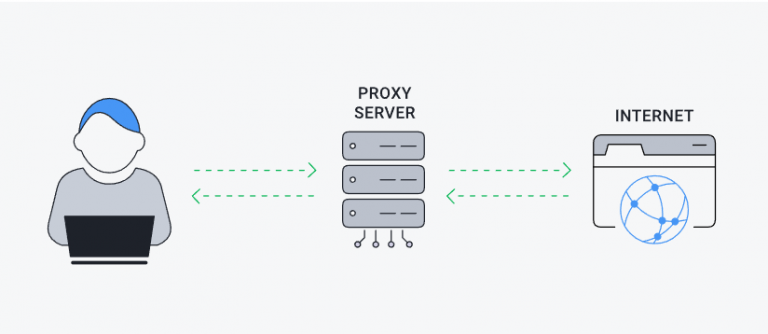
In computer networking , a proxy server is a server application that acts as an intermediary between a client requesting a resource and the server providing that resource. What is a Proxy Server and How Does it Work? The actual nuts and bolts of how the internet…

Nowadays, it is quite common for corporate employees as well as college and high-school students to be unable to access a certain website from their office, campus, or school. The reason for this lies in the fact that most enterprise-level…

Hardware hacking is the modifying of electronics into a form that was not originally intended. This modifying of hardware affects the functionality, components enclosed within the hardware or even the behavior of the hardware equipment itself. These types of modifications…

For many years, passwords were considered to be an acceptable form of protecting privacy when it came to the digital world. However, as cryptography and biometrics started to become more widely available, the flaws in this simple method of authentication became more noticeable. The…
Hashing is an algorithm that generates a fixed-length string from an input. Cryptography is the study of secure communications techniques that allow only the sender and intended recipient of a message to view its contents. The term is derived from the Greek…

Hashing is simply passing some data through a formula that produces a result , called a hash. What is hashing? Hashing is the process of transforming any given key or string of characters into another value. Most popular use for hashing…

A pandemic-focused year made the events of 2020 unprecedented in numerous ways, and the cyber attacks were no different. As the world transitioned to virtual everything — work, school, meetings and family gatherings — attackers took notice. Attackers embraced new…