DALL.E 2: To infinity and beyond sentence-to-image generations.

It’s a set of instructions given to a computer to perform particular tasks


As we all know how much Artificial Intelligence is impacting us in our day to day life. Healthcare is major sector to deploy AI. It generates millions of gigabyte of data, large amounts of money are spent on it for…

In this Article we will learn about an advanced phishing technique called Browser in the Browser or in-short BitB Attack. Introduction A penetration tester and security researcher known as “mr.d0x” recently exposed a phishing technique. Phishing is a cybercrime in…
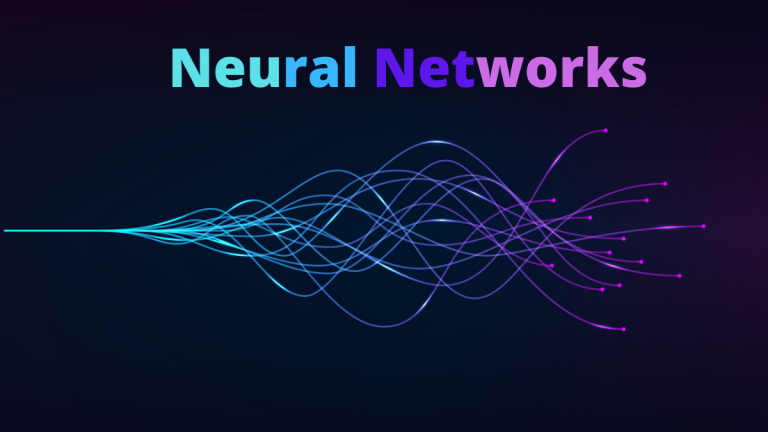
If you are aspiring to learn about Neural networks, then you are at right place. Here I’m going to give a detail note on Artificial Neural network with a common examples. What is Neural Network ? Neural Network is series…

Programming Language As a coder or a programmer, everyone is aware of what is programming languages. A programming language is a computer language a programmer uses to develop software programs, scripts, or other instructions for computers to execute. Although many languages share similarities, each has its own syntax.…
A Kali Linux Tool that Allows You to Hunt Down Usernames! What is Sherlock? Sherlock is a free and open-source device accessible on GitHub. This device is free you can download it from Github and can utilize it for absolutely…
What Is Proof Of Work? Proof of Work (commonly abbreviated to PoW) is a mechanism for preventing double-spends. Most major cryptocurrencies use this as their consensus algorithm. That’s just what we call a method for securing the cryptocurrency’s ledger. Proof…
What is OOPS(Object-Oriented Programming)? OOP treats data as a critical element in the program development and does not allow it to flow freely around the system. It ties data more closely to the functions that operate on it and protects…
Hashcat is a password recovery tool. It had a proprietary code base until 2015, but was then released as open source software. Versions are available for Linux, OS X, and Windows. What is Hashcat Hashcat is the quickest password recovery…

A zero day is a computer software vulnerability either known to those who should be interested in its mitigation or known and without a patch to correct it. Until the vulnerability is mitigate hackers can affect programs, data, additional computers…
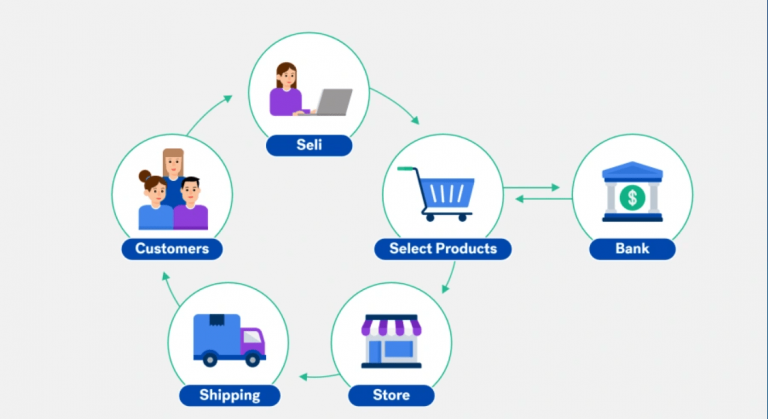
Parameter tampering is a simple attack targeting the application business logic. This attack takes advantage of the fact that many programmers rely on hidden or fixed fields (such as a hidden tag in a form or a parameter in a URL)…
HTTP request An HTTP(HYPER TEXT TRANSFER PROTOCOL) request is made by a client, to a named host, which is located on a server. The aim of the request is to access a resource on the server. To make the request,…

What is API API stands for ‘Application programming interface’. An API is a set of programming codes that enables data transmission between two software products. API allows a programmer to write code to one software, that can then carry out…