HTTP request
An HTTP(HYPER TEXT TRANSFER PROTOCOL) request is made by a client, to a named host, which is located on a server. The aim of the request is to access a resource on the server.
To make the request, the client uses components of a URL (Uniform Resource Locator), which includes the information needed to access the resource. The components of a URL explains URLs.A correctly composed HTTP request contains the following elements:
- A request line.
- A series of HTTP headers, or header fields.
- A message body, if needed.
Each HTTP header is followed by a carriage return line feed (CRLF). After the last of the HTTP headers, an additional CRLF is used (to give an empty line), and then any message body begins.
FOUR Basic Characteristics of HTTP (Hyper Text Transfer Protocol):
- It is the protocol that allows web servers and browsers to exchange data over the web.
- It is a request response protocol.
- It uses the reliable TCP connections by default on TCP port 80.
- It is stateless means each request is considered as the new request. In other words, server doesn’t recognize the user by default.
HTTP headers
HTTP headers are written on a message to provide the recipient with information about the message, the sender, and the way in which the sender wants to communicate with the recipient. Each HTTP header is made up of a name and a value. The HTTP protocol specifications define the standard set of HTTP headers, and describe how to use them correctly. HTTP messages can also include extension headers, which are not part of the HTTP/1.1 or HTTP/1.0 specifications.The HTTP headers for a client’s request contain information that a server can use to decide how to respond to the request.
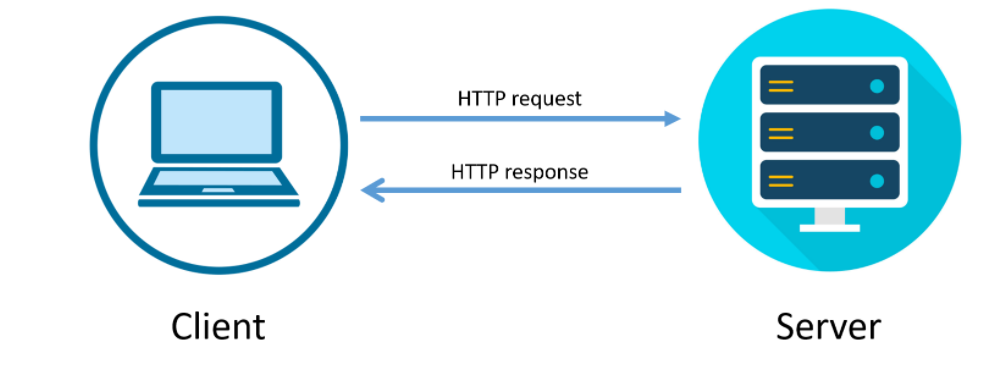
How HTTP request and response works
What you will learn here about HTTP request and response works
- How HTTP request and response works
HTTP communication involves two important terms and those are Client and Server.
Client: Client is the one who makes the HTTP request. For example Browser is the client.
Server: The server is the one who receives the request and sends the response. Basically server is the piece of code that is responsible for accepting the request and sending the response back. usually, the computer on which server code runs is called server.
HTTP request methods
HTTP defines a set of request methods to indicate the desired action to be performed for a given resource. Although they can also be nouns, these request methods are sometimes referred to as HTTP verbs.
GET: This method is used to retrieve specific resource. Requests using GET should only retrieve data and should have no other effect on the data.
POST: A POST request is utilized to send data to a server to create a resource, for example; customer information, file upload etc.
DELETE: As it sounds, the request method is use to delete resources indicated by a specific URI. Making a DELETE request will remove the targeted resource.
CONNECT: This request establishes a tunnel to the server identified by a specific URI, for example; SSL tunneling.
OPTIONS: It permits communication options for a given URL or server. A client can specify a URL with this method, or an asterisk (*) to refer to the entire server.
HEAD: It is same as GET, but doesn’t have a message-body in the response. It’s useful in recovering meta-data which is written according to the headers.
PUT: It is similar to POST as it is also used to send data to the server to create or update a resource. the only difference it has is, it replaces all current representation of the target resource with the uploaded content.
PATCH: The PATCH method is used for making partial changes to an existing resource. The PATCH method provides an entity containing a list of changes to be applied to the resource requested using the URI.
https://thecyberdelta.com/burp-suite/
https://thecyberdelta.com/pegasus/
https://thecyberdelta.com/what-is-tunneling-tunneling-in-networking-useful-of-encapsulation/







