All about Dark web



What Is a Graphics Processing Unit? A Graphics Processing Unit (GPU) is a chip or electronic circuit capable of rendering graphics for display on an electronic device. The GPU was introduced to the wider market in 1999. It is best…
What Is Machine Learning? Machine Learning is a growing technology that enables computers to learn automatically from past data. ML uses various algorithms for building mathematical models and making predictions using historical data or information. Currently, it is being used for…

Panasonic, The Japanese tech company has confirmed data breach after the hackers accessed the personal information of the job candidates and interns. Company said that it network was illegally accessed by a third party on November 11. NHK (Japanese publication)…

A vulnerability in the open source Log4J logging service used by developers to monitor their Java applications first came to light, leaving enterprises scrambling to patch affected systems. Since then, the vulnerability dubbed CVE-2021-44228 has been highly exploited in the wild with…
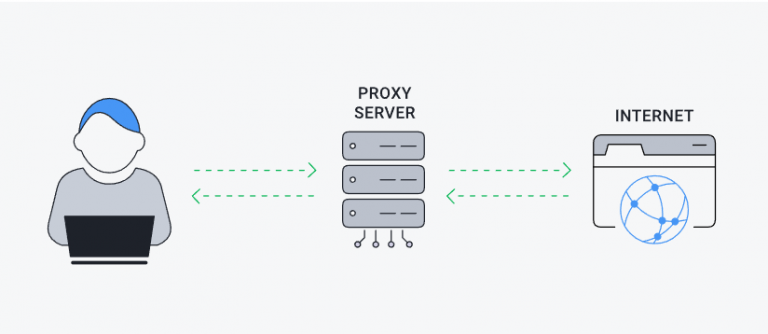
In computer networking , a proxy server is a server application that acts as an intermediary between a client requesting a resource and the server providing that resource. What is a Proxy Server and How Does it Work? The actual nuts and bolts of how the internet…

What is digital forensics? Working in the field of digital forensics has always been “fun.” This is unsurprising, given the increase in public interest inspired by novelists and filmmakers who have made the worlds of digital crime and digital forensics both…

Hashing is simply passing some data through a formula that produces a result , called a hash. What is hashing? Hashing is the process of transforming any given key or string of characters into another value. Most popular use for hashing…

A pandemic-focused year made the events of 2020 unprecedented in numerous ways, and the cyber attacks were no different. As the world transitioned to virtual everything — work, school, meetings and family gatherings — attackers took notice. Attackers embraced new…

A brute force attack uses trial-and-error to guess login info, encryption keys, or find a hidden web page. Hackers work through all possible combinations hoping to guess correctly. What is brute force A brute-force attack is one of the most…
Hashcat is a password recovery tool. It had a proprietary code base until 2015, but was then released as open source software. Versions are available for Linux, OS X, and Windows. What is Hashcat Hashcat is the quickest password recovery…
What is an on-path attacker? On-path attackers place themselves between two devices (often a web browser and a web server) and intercept or modify communications between the two. The attackers can then collect information as well as impersonate either of the…

What is a DNS CNAME record? The ‘canonical name’ record is used in lieu of an A record when a domain or subdomain is an alias of another domain. All records must point to a domain, never to an IP address. Imagine a scavenger…
What is a DNS MX record? A DNS ‘mail exchange’ (MX) record directs email to a mail server. The record indicates how email messages should be routed in accordance with the Simple Mail Transfer Protocol (SMTP, the standard protocol for…
What is a DNS AAAA record? DNS AAAA records match a domain name to an IPv6 address. DNS AAAA records are exactly like DNS A records, except that they store a domain‘s IPv6 address instead of its IPv4 address. IPv6 is the…