
Keylogger – The Surveillance Tool (2022)
If you have searched about keyloggers and want to learn about them then you are…

If you have searched about keyloggers and want to learn about them then you are…
Cyberterrorism is defined as the strategically premeditated attack over the internet that mainly focuses over…

Panasonic, The Japanese tech company has confirmed data breach after the hackers accessed the personal…

A vulnerability in the open source Log4J logging service used by developers to monitor their…
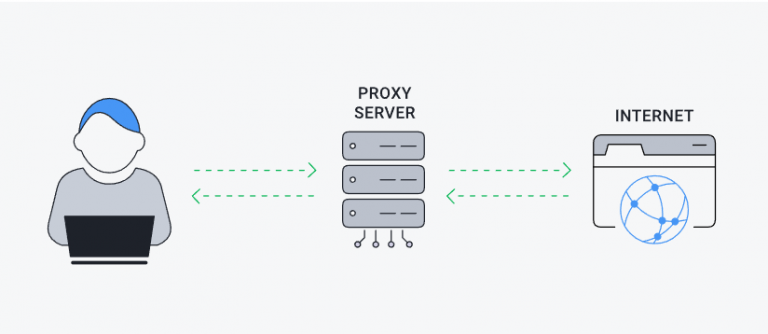
In computer networking , a proxy server is a server application that acts as an intermediary between a client requesting…

Quickly mapping an organisations attack surface is an essential skill for network attackers (penetration testers,…

What is digital forensics? Working in the field of digital forensics has always been “fun.” This…

Artificial Intelligence is the future. AI, there are a lot of debates lying and floating…

Nowadays, it is quite common for corporate employees as well as college and high-school students…

Hardware hacking is the modifying of electronics into a form that was not originally intended.…

For many years, passwords were considered to be an acceptable form of protecting privacy when…
Hashing is an algorithm that generates a fixed-length string from an input. Cryptography is the study…

Hashing is simply passing some data through a formula that produces a result , called a…

What Is Proof Of Concept? The Blockchain Proof of Concept is a process of determining…
What Is Proof Of Work? Proof of Work (commonly abbreviated to PoW) is a mechanism…