Proxy Server
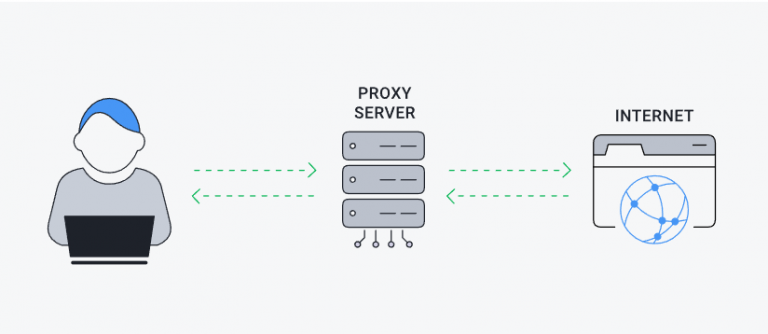
In computer networking , a proxy server is a server application that acts as an intermediary between a client requesting a resource and the server providing that resource. What is a Proxy Server and How Does it Work? The actual nuts and bolts of how the internet…