Passwords are the first line of defense that fights against unauthorized access to your computer and your personal data. No other users can read, delete or change your data without knowing your password. But why is password security required?
As an ever increasing number of monetary exchanges happen electronically, the difficulties and stakes develop. Its an obvious fact that over-the-air burglary of information is an enormous issue, yet data fraud and through and through breaks likewise imply developing dangers.

Fortunately — yet past the point of no return — the U.S. government has given guidelines that will compel vendors, beginning in October, to utilize safer terminals outfitted with chip perusers as opposed to depending on attractive strip cards. The punishment for not having a chip and mark framework set up? Shippers are on the snare for any extortion or robbery.
These frameworks, similar to Apple Pay, create one-time codes that make information burglary more troublesome. They cut extortion by a normal of 55 to 70 percent. In any case, they miss the mark regarding chip and PIN innovation that the Federal Reserve says is 700% safer. As a matter of fact, a November 2014 investigation discovered that 82% of U.S. buyers support chip and PIN installment cards.
In the mean time, telecom firm Telstra found that shoppers need more powerful assurances. This incorporates voiceprint and unique finger impression biometrics rather than client names and passwords.
For the present, this appears to be a far off dream. While a few monetary administrations firms and others have gone to Touch ID on the iPhone and different gadgets, these devices are for the most part for comfort. They dispense with secret word section at login however the secret word actually exists. Sadly, passwords are the 21st century adaptation of skeletons keys. Eventually, we can’t keep on pitching down the way of close to add up to disappointment.
Astoundingly, the Telstra investigation discovered that one out of four U.S. buyers would try and think about imparting their DNA to their monetary organization, assuming it implied it would make verification simpler and their monetary and individual data safer.
Telstra likewise found that loan costs and simplicity of getting to reserves used to be the main contemplations while choosing a monetary organization. In any case, today, the greater part of U.S. customers refer to the security of their funds and individual data as their first concern, along with their establishments’ standing for security.
The primary concern for CIOs and other business pioneers? Shoppers progressively incline toward organizations that guard their information — or if nothing else do all that could be within reach to amplify security. Now is the ideal time to execute more rigid security, remembering voice biometrics for contact focuses and in applications. Over the course of the following ten years, almost certainly, associations that fall behind will find clients and incomes heading somewhere else.
Data Sharing and Security Issues
On account of present day innovation, figuring gadgets come in a wide range of structures, for example, work area machines, PCs, cell phones, music players, and tablets. Any of these gadgets might associate with other figuring gadgets and offer data, and by and large, they may likewise interface with banks to manage monetary exchanges. These machines are possibly powerless against abuse by unapproved clients, and in this way, clients ought to constantly safeguard them with passwords.
Passwords are a method by which a client demonstrates that they are approved to utilize a registering gadget. A solitary gadget might have different clients, each with their own secret phrase. Passwords are similar to a lock-and-key situation, wherein just the right key will empower an individual to approach. The thing that matters is that every individual has an alternate key for a similar entryway.
Some registering gadgets, like work stations and PCs, likewise have an administration level client, or “superuser,” who can handle different clients and change the processing gadgets programming, in addition to other things. This superuser account is otherwise called the “root” or “executive” account. This is critical to know on the grounds that while programmers will attempt to secure any secret key they can get, they will by and large attempt to figure the superuser secret word first, as it gives them the most command over a gadget.
Significance of a Strong Password
One of the worries that individuals frequently have with regards to making complex passwords is an apprehension about failing to remember them, especially when there are a memorable few. Normally, an individual ought to attempt to consider something that will be simple for them to remember.
One method for doing that is to transform a sentence or expression into something not handily perceived by others. To do this, utilization the main letter of each and every word in the sentence, supplanting specific words with numbers or images. For instance, “for” might be supplanted with the number 4 or “number” with the # image. With this strategy, a secret key, for example, “Save the number for later in the year” may understand St#4LITY.
Protection Strategies
We as a whole realize that the further sophisticated a secret key is, the better. They ought to incorporate a combination of figures, emphasis imprints and images, and subsidized and lowercase letters.
Or on the other hand would it be judicious for them?
Late disquisition into secret expression security has shown that quite a bit of customary secret word sapience is not just out- base, yet potentially dangerous.1
Facebook, Twitter, Yahoo, and LinkedIn have all succumbed to online assaulters who have taken whole information bases brimming with watchwords. The watchwords are mixed for security, yet this offers little solace when PC systems can make a huge number of conjectures in only a couple of hours. Since utmost watchwords depend on words in a word reference joined with a number or image, it can take these ultramodern systems indeed less chance to hack them.
The outgrowth is that normal secret expression strategies do not avert the burglary of numerous guests’ watchwords, which makes a mind boggling, ultramodern, and worthwhile shadow assiduity. In all honesty, taken watchwords can get enormous cash on the dark request.2
All by each, what is the significance then to you? It implies that each secret expression you’ve made is a significant and weak earthenware worth securing.
To do as similar, you ought to go a stage past picking watchwords that are delicate for a mortal to figure. Your watchwords need to likewise be hard for a PC to sort out. Then are a many hints.
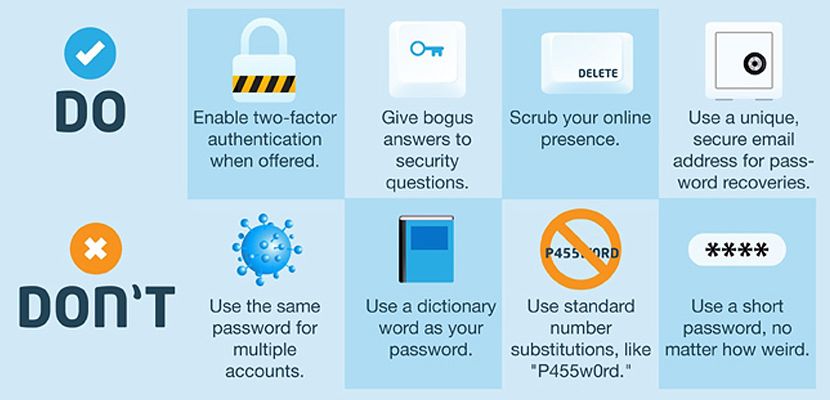
Favor Length Over Complexity
Longer Watchwords are more grueling to break. At least 12 characters is suggested. Consider hanging together the two or three letters of a most favored film statement, tune verse, or sonnet. For extra-delicate records, it might feel OK to change your watchwords constantly. In the event that you like the possibility of ideal secret word assurance, yet concern you won’t have the option to deal with numerous, regularly evolving watchwords, secret expression chiefs can help you with coordinating, store, and use multitudinous watchwords safely.3
No Plain English
Straightforward series of figures, alongside watchwords that can be tracked down in the word reference, are the least demanding to break. Microsoft proposes that your secret word ought to contain at least one subsidized and lowercase characters, figures, images, and indeed unicode characters.
Stir It Up
Numerous individualities use analogous secret expression for colorful records since it’s memorable’s simpler. In any case, this could prompt serious issues. You may not be too upset about the individual data put down in your LinkedIn or Twitter accounts, still what might do assuming programmers employed your compromised secret key to get to your dispatch, financier, or checks? In the event that you witness difficulty recalling different watchwords, you might need to keep a rundown on your PC, yet do not store it on your work area or in your inbox. Give the document a deceptive name and cover it in an envelope where no bone but you can track down it.
A secure secret key can not live. In any case, putting individual data behind a abecedarian secret word resembles leaving your Porsche in a parking area with your keys on the scramble. By going to protection lengths to fortify your secret key, you might have the option to help with defending your delicate individual information and your security.
Read the password policy given by the Ministry of Electronics and Information Technology.







