Chatbot are the thing that act as bridge between user to user or user to a organization for communication. When face to face interaction is not possible we use our technology to communicate with others. Auto technology of speech recognition like Alexa and Siri are used for response. Now we are using chatbots for communicating with people. It is user friendly and more efficient for communicating with others.
What is a Chatbot ?
Chatbot is an application that interacts with humans through user command. In simple terms it is an extension of existing Human Interface Mediums (HIMs), such as mobile phones and the internet. It is an artificial application that uses precalculated user phrases and auditory or text-based signals to simulate interactive human conversation.
Chat bots are used in mostly social networks and instant messaging applications. These chatbots provide a way to communicate with the customers or service providers via a messenger or bot. The other names for this chat bot are talk bot and chatter bot. These chats are for small queries and general purposes. If the customers enquiry is beyond the chat box then service provider send a human operator.

These chat bots are commonly used in online messaging apps. Chatbots can carry out many tasks and responding to human requests. These chatbots are used in various fields of AI, machine learning, healthcare, software field and other industries. These chatbots understand the queries of the user and replies to the user as the request received. Now a days, many customers use digital communication channels and they appreciate a chatbots advantage such as 24/7 customer service, personalized interaction, and no waiting time.
For companies chat bots are like cost saving as many processes are repeated and can be automated and employees can be dedicated to more complex tasks. Large companies like Google, Facebook and IBM are working on improving their chatbots to make user gets more interaction. The most well know examples are the question and answering systems like Siri, Alexa, Cortana and Googles recent chat bot Meena. The primary goal of these are to develop voice assistances based on natural learning process and machine learning methods.
Many chat bots are used for online stores, banks, industrial technical support, and so forth, are created by small or large companies. Such chat bots are called closed-domain chatbots. These chatbots respond in different ways to different keywords. Technical solutions vary from company to company and user to user. So they use clients knowledge, such as webpage, manuals, FAQs, documents, human – human transcriptions and use this knowledge to create chatbots specific to tasks suited o the given company. Big companies create open domain chat bot and small companies create closed domain chat bot.
Security and Privacy in chat bots
Threats and vulnerabilities are of two types. A security threat is defined as a risk by which an organization and its systems can be compromised. Security threats are identified by a STRIDE model as spoofing, Tampering, Repudiation, Information Disclosure, Denial of service, Elevation of Privilege’s, and many more; every security threat should be reduced by protective mechanisms ensuring the following properties as Authenticity, Integrity, Non-repudiation, Confidentiality, Availability, Authorization, and many more.
Security will be weakened when the coding is weak, lack of current drivers on hardware side, has a weak firewall, and so fourth. Human errors mostly cause system vulnerabilities. Many chatbots use cloud computing services, which have threats and vulnerabilities very well handled, to store data, the following text is focused on communication part and different aspects of data manipulation.
Secure messages can be divided into two parts. One is secure transformation of data, that is secure transformation of images, voice, messages, to a server on which the chatbot is hosted. The second one is users data on the server, that is how data is processed, stored and shared. These two things are the life cycle of user’s domain. So in order to keep information much safer in chatbots we use some methods cover any communication with the chatbots, such as pop-up chat window in a web browser or mobile application.
Authentication and Authorization
Conformation of user identity is not necessary in all situations. if a user asks for help, for example in a shopping website then no authentication is needed. But when the user asks help on banking system like checking account balance then we must verify the user and verified with user credentials. After every login the credentials must be given a token for a particular period of time. The system must create a new token after a given period.
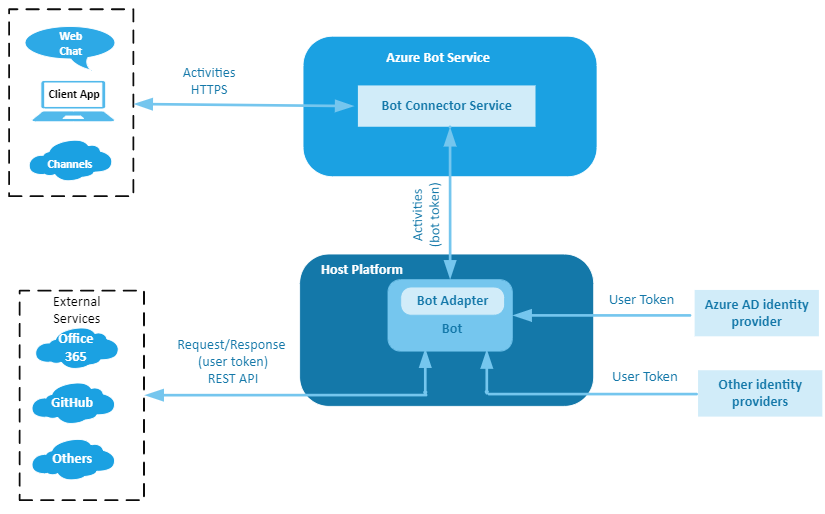
The greater protection can be given by two factor authentication, for example the user is asked to verify the authentication of account credentials through an email and text messages There are multi-factor authentication schemes, which can be used rarely during the login and conversation with a chatbot. In short authentication ensures that the correct person has access to the right data and services and authentication is necessary when a chatbot works with a user’s data.
End-to-End Encryption
End-to-End Encryption is a system of communication where only the communication parties can read the messages. These conversations are encrypted in such a way that only one recipient of a message is allowed to decrypt it, and not anyone in between. It is important that only the involved parties have access to the cryptographic keys requires to decrypt the conversation.
In the case of [public key encryption, the user’s device generates a key pair, private and public. There are different protocols to provide encryption, such as the RSA algorithm. The public key is used to encrypt the message and the corresponding private key can decrypt these messages. Naturally, the public key can be used by anyone sending a message to the owner of the private key. It is very important to keep a user’s private key secure, otherwise an attack can decrypt all messages intended for that user.
Self-destructing messages
In many cases when sensitive PII (personally identifiable information) is transmitted, self destructing messages are a practical solution. Messages containing PII are automatically deleted after a specific period of time. This can involve both parties: the user and the chatbot. Self-destructing messages are an important safety practice when communicating with financial (banking) and healthcare chatbots. Specifically the GDPR stipulates that personal data must not be kept longer than is necessary for the purposes for which they are processed. The general conversation is not personal, but financial and health data. It is not easy for a chatbot to distinguish between personal information, but this is also determined by GDPR and protected Health Information protecion50 is defined by US law.
Check here to get more information about security issues of chatbots
https://onlinelibrary.wiley.com/doi/full/10.1002/cpe.6426
How Chatbots are Protected ?
People often express concerns about the safety of new technology. Chatbots have been around for quite sometime, but many people still don’t know about them. Meanwhile, the rise in cybercrime around the world is cause for concern. You should evaluate and determine if these systems are designed to protect yours user’s sensitive data.
The way technology is secured in the financial sector complies with industry norms and regulations, including the protection of third-party customer information. Users can now use chatbots to check their bank account balances on social networks such as Facebook, avoiding lengthy verification processes.
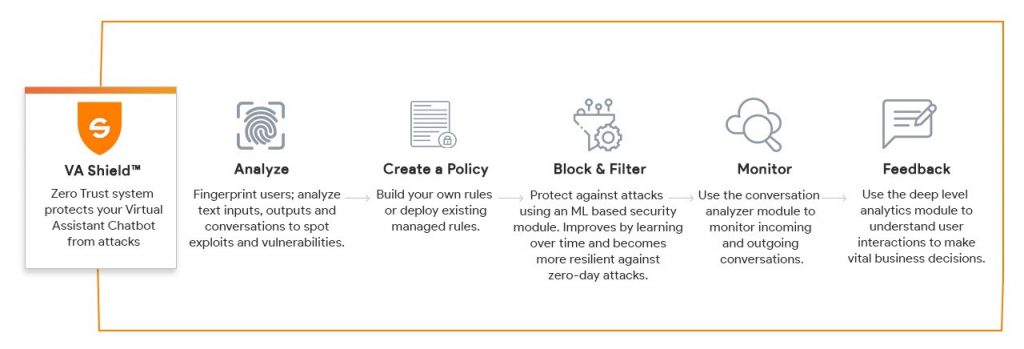
Authentication and authorization, on the other hand, are protected by these bots. The user’s girlfriend’s identity must be verified before any information is shared. Users receive token that expires after certain amount of time and can be used to initiate payments. However. after some time has passed without using it a new one will be crated. Chatbots further protected by a biometrics procedure where the users fingerprint is compared to those previously recorded by the system before access is granted. It has been proven that no two people, even identical twins, have the same fingerprints. This makes the biometric authentication process secure.
Another way to protect consumers from scammers who think they are smart is for chatbots to completely remove conversations between consumers and users. After the discussion ends, the system will delete all information so that no one can follow it.
Security Risks of Chatbots
Chatbot security risks fall into two categories, one is threats and vulnerabilities.
The one-time events such as malware and distributed denial of service (DDoS) attack are called threats. There will always be targeted attacks on business, resulting in employees being locked out. The threat of consumer data breaches is on the rise, highlighting the risks of using chatbots.
A vulnerability, on the other hand, is a flaw in a system that allows cybercriminals to break into the system. Both go hand in hand because vulnerabilities allow threats to penetrate a system.
These are the result of coding mistakes, security vulnerabilities, and user errors. And it’s nearly impossible to create a system that can’t be hacked, because it’s hard to design a system that works. Chatbot development is typically starts with code and is tested for every-present cracks, These tiny cracks go unnoticed until it’s too late, but cybersecurity professionals should be able to identify them.
Threats
There are many threats. For example, some of the threats could be employee impersonation, ransomware and malware, phishing, whaling and repurposing of bots by hackers.
1. Ransome
As the name suggests, ransomware is a form of virus that encrypts a victim’s files and threatens to expose their data unless a ransom is paid.
2.Malware
It is a software designed to cause harm to any device or server. Ransomware, for instance, is type of malware. Other examples include Trojan viruses, spyware and Adware, among others.
3.Phishing
It is fraudulent act of seeking sensitive information from people by posing as legitimate institutions or individuals. Usually, people ask for sensitive details such as personally identifiable information, banking and credit card details, etc.
4. Whaling
It is similar to phishing, but people seeking sensitive content target high-profile and senior employees within the company.
These are some common examples of threats associated with chatbots. Such threats may lead to data theft and alterations, along with impersonation of individuals and re-purposing of bots.
Vulnerabilities
Un encrypted chats and a lack of security protocols are the vulnerabilities that pace the way for threats.
Hackers may also obtain back-door access to the system through chatbots if there is an absence of HTTPS protocol. However, sometimes the issue are present in the hosting platform.
Ways to secure Chatbots
Other than the security things discussed above like End-to-End encryption, Authentication process, Biometric authentication, Two factor Authentication there are some other methods to secure chatbots. They are:
User ID Authentication
The oldest way to create security are still valid and will continue to be. We all remember getting creative with User IDs as kids. This is the easiest and most effective way to protect your account. Creating a unique user ID is the most common security method for the most people. Few things can get past a secure credentials with a strong password that uses uppercase and lowercase letters, numbers, and symbols.
Authentication Timeout
A ticking clock during the authentication processes provides a higher level of security. In this case, the validation tokens expiration is limited to a fixed amount of time. A time sensitive code will be sent to the users email id/phone number when the user attempts access. Access is revoked when the token expires. This prevents repeated attempts to access the data.
Process and Protocol
You see most of the webpages say “HTTPS” at the top. This is because it is the default setting for the security system. Security teams should ensure that all data transfers occur over HTTP and encrypted connections. As long as Transport Layer Security or Secure Sockets Layer does its job of protecting these encrypted connections, organizations need not worry about braking in.
Education
Human error is one of the leading causes of cybercrime and educating people about it is very important. A combination of fundamentally flawed systems and naïve users allows hackers open access to systems. Despite the increasing recognition of the importance of rooting out cybercrime in recent years, customers and employees are still the most vulnerable to errors. Unless everyone is educated on how to use conversational chatbots safely, security remains an issue. An effective chatbot security strategy should include training workshops by IT professionals on key topics. It improves your employee’s skills. Additionally, encourage your customers to trust your chatbot security system. Even if your chatbot security system. Even if you cant train your customers, you can provide a roadmap or instructions on how to navigate the system to avoid problems.
Uses of Chatbots
- Online shopping : In these environments, sales team can use chatbots to answer simple product questions or provide useful information that consumers can later search for shipping rates or availability.
- Customer service : Service departments can also use chatbots to help service agents answer repetitive requests. For example, a service representative can give a chatbot an order number and ask when the order has shipped. Chatbots typically transfer calls or texts to a human service agent when a conversation becomes too complex.
- Virtual Assistant : Chatbots can also act as virtual assistants. Apple, Amazon, Google, and Microsoft all have forms of virtual assistants. Apps like Apple’s Siri and Microsoft’s Cortana, and products like Amazon’s Echo with Alexa and Google Home, all act as personal chatbots.
For more information about chat bots go for the following link
https://towardsdatascience.com/hidden-privacy-risks-of-chatbot-conversations-881dbeeb98a
Also check on the latest article of our website following the link given below