DDoS (Distributed Denial of Service) is a cyber attack attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with flood of internet traffic.
What is DDoS
The flood of incoming messages, connection request or malformed packets to the target system forces it to slow down or even crash and shut down.
How does DDoS works?
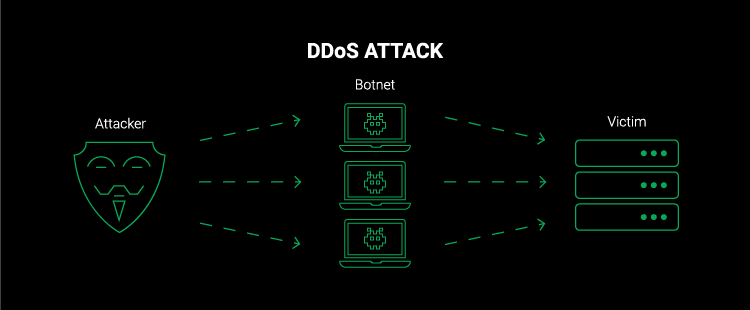
Networks like webs severs have a limit to number of request which they can service simultaneously. The channel which connects the server to internet will also have a limited bandwidth/capacity. When the number of request exceeds the capacity (crosses the limit of bandwidth) limit of any component of infrastructure then the level of service is much likely to suffer.
The responses to requests will be much slower than normal, many user request would be totally ignored. Once a botnet has been established, the attacker is able to direct an attack by sending remote instruction to each bot.
Targets for DDoS attack:
- Server
- Any internet shopping sites
- Business which deepened on online service
- Online Organizers
- Online Casinos
Main types of DDoS attack:
- Application layer – Top most layer that specifies protocols for interactions with the network.
- Presentation layer – It makes sures that data is in usable format and is where data encryption occurs.
- Session layer – It manages the open network sessions intended for particular exchanges.
- Transport layer – Transmit data using transmission including TCP and UDP.
- Network layer – This is responsible for routing data packets through intermediaries like routers and server.
- Data link layer – Organizes the data into the packet that are ready to be sent.
- Physical layer – Defines transmission of raw bits over the physical data links.

Few ways to stop DDoS
Monitoring your traffic to look for abnormalities, including unexplained traffic spikes and visits from suspect IP address and geolocations. All of these could be signs of attackers performing “dry runs” to test your defenses before committing to a full-fledged attack. Recognizing these for what they are can help you prepare for the onslaught to follow.
Keep an eye on social media (particularly Twitter) and public waste bins (e.g., Pastebin.com) for threats, conversations and boasts that may hint on an incoming attack.
Consider using third-party DDoS testing (i.e., Pen Testing) to simulate an attack against your IT infrastructure so you can be prepared when the moment of truth arrives. When you undertake this, test against a wide variety of attacks, not just those with which you are familiar with.
Create a response plan and a rapid response team, meaning a designated group of people whose job is to minimize the impact of an assault. When you plan, put in place procedures for your customer support and communication teams, not just for your IT professionals.
Note: To truly protect against modern DDoS attacks, you should use a DDoS mitigation solution. Solutions can be deployed on-premises, but are more commonly provided as a service by third-party providers. We explain more about DDoS mitigation services in the following section.
Process of mitigating DDoS attack
The key concern in mitigating a DDoS attack is differentiating between attack traffic and normal traffic.

For example, if a product release has a company’s website swamped with eager customers, cutting off all traffic is a mistake. If that company suddenly has a surge in traffic from known attackers, efforts to alleviate an attack are probably necessary.
The difficulty lies in telling the real customers apart from the attack traffic.
In the modern Internet, DDoS traffic comes in many forms. The traffic can vary in design from un-spoofed single source attacks to complex and adaptive multi-vector attacks.
A multi-vector DDoS attack uses multiple attack pathways in order to overwhelm a target in different ways, potentially distracting mitigation efforts on any one trajectory.
An attack that targets multiple layers of the protocol stack at the same time, such as a DNS amplification (targeting layers 3/4) coupled with an HTTP flood (targeting layer 7) is an example of multi-vector DDoS.
Mitigating a multi-vector DDoS attack requires a variety of strategies in order to counter different trajectories.
Generally speaking, the more complex the attack, the more likely it is that the attack traffic will be difficult to separate from normal traffic – the goal of the attacker is to blend in as much as possible, making mitigation efforts as inefficient as possible.
Mitigation attempts that involve dropping or limiting traffic indiscriminately may throw good traffic out with the bad, and the attack may also modify and adapt to circumvent countermeasures. In order to overcome a complex attempt at disruption, a layered solution will give the greatest benefit.
Blackhole routing:
One solution available to virtually all network admins is to create a blackhole route and funnel traffic into that route. In its simplest form, when blackhole filtering is implemented without specific restriction criteria, both legitimate and malicious network traffic is routed to a null route, or blackhole, and dropped from the network.
If an Internet property is experiencing a DDoS attack, the property’s Internet service provider (ISP) may send all the site’s traffic into a blackhole as a defense. This is not an ideal solution, as it effectively gives the attacker their desired goal: it makes the network inaccessible.
Rate limiting:
Limiting the number of requests a server will accept over a certain time window is also a way of mitigating denial-of-service attacks.
While rate limiting is useful in slowing web scrapers from stealing content and for mitigating brute force login attempts, it alone will likely be insufficient to handle a complex DDoS attack effectively.
Nevertheless, rate limiting is a useful component in an effective DDoS mitigation strategy.
Web application firewall:
A web application firewall (WAF) is a tool that can assist in mitigating a layer 7 DDoS attack. By putting a WAF between the Internet and an origin server, the WAF may act as a reverse proxy, protecting the targeted server from certain types of malicious traffic.
By filtering requests based on a series of rules used to identify DDoS tools, layer 7 attacks can be impeded. One key value of an effective WAF is the ability to quickly implement custom rules in response to an attack.
Anycast network diffusion:
This mitigation approach uses an Anycast network to scatter the attack traffic across a network of distributed servers to the point where the traffic is absorbed by the network.
Like channeling a rushing river down separate smaller channels, this approach spreads the impact of the distributed attack traffic to the point where it becomes manageable, diffusing any disruptive capability.
The reliability of an Anycast network to mitigate a DDoS attack is dependent on the size of the attack and the size and efficiency of the network. An important part of the DDoS mitigation implemented by Cloudflare is the use of an Anycast distributed network.
Cloudflare has a 121 Tbps network, which is an order of magnitude greater than the largest DDoS attack recorded.
If you are currently under attack, there are steps you can take to get out from under the pressure. If you are on Cloudflare already, you can follow these steps to mitigate your attack.
The DDoS protection that we implement at Cloudflare is multifaceted in order to mitigate the many possible attack vectors. Learn more about Cloudflare’s DDoS protection and how it works.
Companies suffered by DDoS attack
The Google Attack – 2020
On October 16, 2020, Google’s Threat Analysis Group (TAG) posted a blog update concerning how the threats and threat actors are changing their tactics due to the 2020 U.S. election.
At the end of the post, the company snuck in a note: in 2020, our Security Reliability Engineering team measured a record-breaking UDP amplification attack sourced out of several Chinese ISPs (ASNs 4134, 4837, 58453, and 9394), which remains the largest bandwidth attack of which we are aware.
Mounted from three Chinese ISPs, the attack on thousands of Google’s IP addresses lasted for six months and peaked at a breath-taking 2.5Tbps!
Damian Menscher, a Security Reliability Engineer at Google, Wrote: The attacker used several networks to spoof 167 Mpps (millions of packets per second) to 180,000 exposed CLDAP, DNS, and SMTP servers, which would then send large responses to us. This demonstrates the volumes a well-resourced attacker can achieve: This was four times larger than the record-breaking 623 Gbps attack from the Mirai botnet a year earlier.
AWS ATTACK – 2020
AWS reported mitigating a massive DDoS attack in February of 2020. At its peak, this attack saw incoming traffic at a rate of 2.3 terabits per second (Tbps). AWS did not disclose which customer was targeted by the attack.
The attackers responsible used hijacked Connection-less Lightweight Directory Access Protocol (CLDAP) web servers. CLDAP is a protocol for user directories. It is an alternative to LDAP, an older version of the protocol. CLDAP has been used in multiple DDoS attacks in recent years.
GIT HUB ATTACK – 2018
One of the largest verifiable DDoS attacks on record targeted GitHub, a popular online code management service used by millions of developers. This attack reached 1.3 Tbps, sending packets at a rate of 126.9 million per second.
The GitHub attack was a Memcached DDoS attack, so there were no botnets involved. Instead the attackers leveraged the amplification effect of a popular database caching system known as Memcached. By flooding Memcached servers with spoofed requests, the attackers were able to amplify their attack by a magnitude of about 50,000x.
Luckily, GitHub was using a DDoS protection service, which was automatically alerted within 10 minutes of the start of the attack. This alert triggered the process of mitigation and GitHub was able to stop the attack quickly. The massive DDoS attack only ended up lasting about 20 minutes.
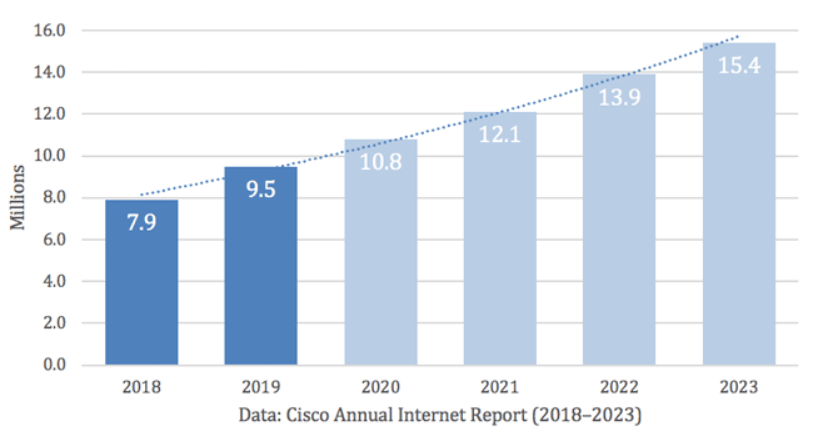
European Gambling Company – 2021
In February of 2021, Akamai dealt with “three of the six biggest volumetric DDoS attacks” that have ever been recorded. The most recent of these attacks peaked at 800Gbps, which was targeted at a gambling company in Europe. The perpetrators used the Datagram Congestion Control Protocol (DCCP) or protocol 33, which, according to Akamai, is a new DDoS attack vector. The attackers leveraged the DCCP for DDoS, which lead to a volumetric attack and has the ability to bypass the defences set up for the TCP and UDP traffic flows.
The Cloudflare Attack – 2014
In 2014, Cloudflare, a cybersecurity provider and content delivery network, was slammed by a DDoS attack estimated at approximately 400 gigabits per second of traffic. The attack, directed at a single Cloudflare customer and targeted on servers in Europe, was launched using a vulnerability in the Network Time Protocol (NTP) protocol, which is used to ensure computer clocks are accurate. Even though the attack was directed at just one of Cloudflare’s customers, it was so powerful it significantly degraded Cloudflare’s own network.
https://www.thecyberdelta.com/cve-2022-0847-dirty-pipe/
https://www.thecyberdelta.com/http-requesthyper-text-transfer-protocol/







