If you want to learn about the WPScan tool and its uses then you are at the right place here in this article I will try my best to explain and cover everything about this tool and also give some supportive links by which you can get some extra information which might not be there in this article.
What is WPScan?
WPscan is a tool specially designed to scan vulnerabilities or get information about a WordPress website. It is free for non-commercial use and paid for commercial use. It is mainly used by bloggers and security professionals to scan and test the security of their WordPress websites.
What can this tool check for?
WPScan can check the version of WordPress installed and its vulnerabilities. It can find which plugins are installed and also which themes are installed and their associate vulnerability. It can also find username enumeration and users with weak passwords via password brute forcings and other methods and has the capability to dump databases that may be publicly accessible.
Options in this tool
There are multiple options in this tool that are displayed if you use the command wpscan -h or wpscan –help but as I have already told you that you will learn almost everything in this post so I am mentioning some of the important and useful commands here.
- –url <URL> : The URL of the blog to scan( Allowed Protocols: http, https; default Protocol if none provided: http this option is mandatory unless update or help or hh or version is/are supplied)
- –version : Display the version and exit
- -o or –output FILE : Output to FILE
- -f or –format : FORMAT Output results in the format supplied (Available choices: json, cli, cli-no-colour, cli-no-colo )
- –wp-content-dir DIR : The wp-content directory if custom or not detected, such as “wp-content”
- –wp-plugins-dir DIR : The plugins directory if custom or not detected, such as “wp-content/plugins”
- -e, –enumerate [OPTS] : Enumeration Process
These are the most essential and used options in WpScan. Here enumeration also contains different options which will be explained further.
Enumerate
Enumerate Modes
Enumerating a WordPress website can be done in 3 ways that are: Passive, Aggressive, and Mixed. Here Mixed is the default mode that gives the most results. If the server doesn’t have the capability to handle huge loads then use passive mode and aggressive mode are used to get more information in a less fraction of time but sometimes this mode skips some important things which may be needed for you.
Enumerate Options
WPScan can enumerate various things from a WordPress website, such as plugins, themes, usernames, backed up files wp-config.php files, Timthumb files, database exports, and more. To use its enumeration capabilities to supply the -e option. Some important options are given below.
vp(Vulnerable plugins)ap(All plugins)p(Popular plugins)vt(Vulnerable themes)at(All themes)t(Popular themes)tt(Timthumbs)cb(Config backups)dbe(Db exports)u(User IDs range. e.g: u1-5)m(Media IDs range. e.g m1-15)
If no option is supplied to the -e flag, then the default will be: vp,vt,tt,cb,dbe,u,m
How to install WPScan in Linux?
If you are using Kali Linux then it is a preinstalled tool but in the case of other linux you can install it by following the steps below-
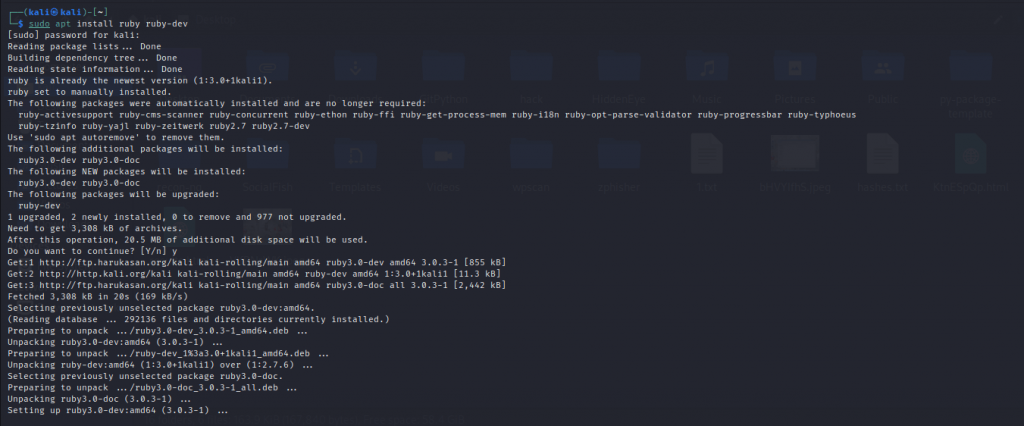
First of all, we need ruby to be get installed to run wpscan so install it by giving the command.
$ sudo apt install ruby ruby-dev
Type the password and hit enter then press y and continue. It will automatically install the application.
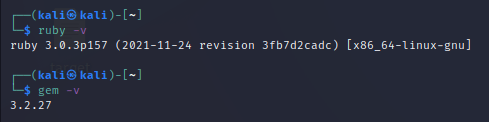
To confirm the installation and check its working properly with gem feature type the command.
┌──(kali㉿kali)-[~]
└─$ ruby -v
┌──(kali㉿kali)-[~]
└─$ gem -v
If the versions of this are showing then it is confirmed that it was successfully installed.
Now it is time to install the WPScan tool by using the command given below.
$ sudo gem install wpscan
It will automatically install the tool.
Now the application has been successfully installed in your linux now you can use the command to get the desired information.
Scan a website with WPScan Tool
If you want to scan a website then simply type the command
$ wpscan --url <Website Link>In my case, I have used
$ wpscan --url https://www.thecyberdelta.com
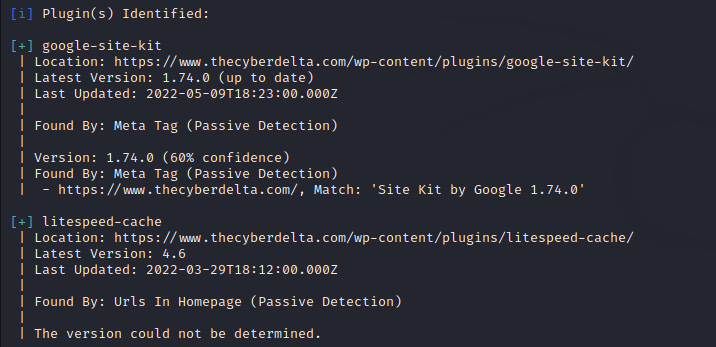
Besides this, you can get much such information about a website as well as the vulnerabilities of the website using its API key and there are many commands to get different information about a website.
Conclusion
I hope you got knowledge about this tool but there must be some more things about this tool that I have missed so I am attaching some links you can also follow to get additional knowledge about this tool.
- https://en.kali.tools/?p=282
- https://github.com/wpscanteam/wpscan/wiki/WPScan-User-Documentation
- https://github.com/wpscanteam/wpscan
If you are interested in hacking and want to get deep knowledge about that then you should see our other articles such as 888 RAT- The Payload Creator and Keylogger – The Surveillance Tool (2022).