
What we are going to see about Nessus.
In the following purview, we are going to talk about Nessus. A cybersecurity software, which scans vulnerability and penetrates testing in your system. Learn what is it? why should you use it? how does it protect us? it’s downloading on Linux, Mac, and windows OS. and gather some basic knowledge about it too !!
How to scan your vulnerability, and the basics of Nessus.
One single vulnerability is all the attacker needs(use Nessus)!!
We live in an age where many of us are directly or indirectly depending upon cybersecurity. With the growing crime rates, it has become a necessity to install an antivirus or a malware detector. When was the last time you had to install or update one on your computer? updates on computers will always be very important and consistent. In this article, we are going to talk about Nessus, so what is Nessus ??
Nessus is one of the many vulnerability scanners used during vulnerability assessments and penetrating testing engagements, including malicious attacks. why do we need them? with that new bugs and vulnerabilities are found every day or weakness in our networks. We get tracked and followed and sometimes hacked too!!
How does Nessus protect us? Nessus test each port on the computer, determining, what service it is running and then testing this service to make sure there are no vulnerabilities in it, that could be used by a hack to carry out the malicious attack.
Renaud Deraison created, Nessus twenty-three years ago, the scan engine was designed to be physically attached to hubs and switches, changed infrequently, and was always available unless somebody shut their system down for the weekend.
Fast forward to the current day: Almost every organization has a cloud-first strategy and new workloads can be spun up and down in minutes across the globe with just a few clicks. The Nessus is owned by tenable inc., its headquarters are located in Columbia Maryland USA.
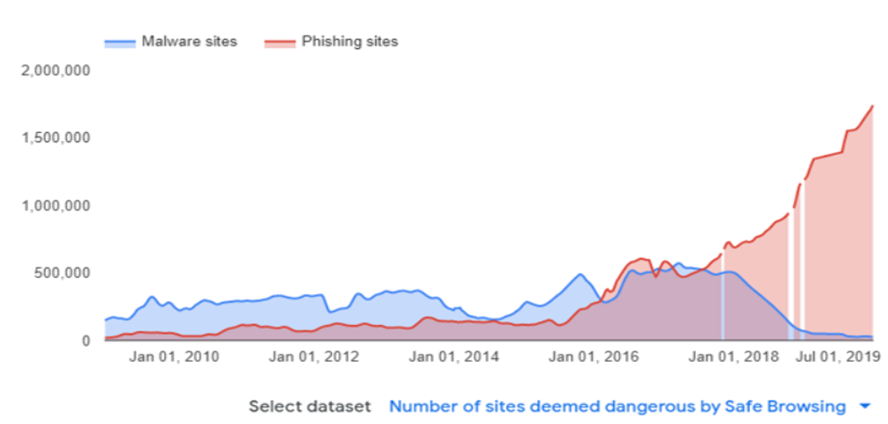
The image above shows the growth in malware increase across the world.
After the covid pandemic, it’s seen that there is a sudden increase in malicious attacks and hacking. So how do we get started?
Well, you can download nesses in Linux, Windows, and Mac operating system
we will be downloading it on windows os, let’s download the windows version. You’ll find the 64-bit version as well almost at the end of the section. 8.12.0 was released on Oct 8,77 megabytes, just click on it. You can download it and accept the user agreement. and accept further conditions and push forward to the installation.
Now choose essential, put on your information. Soon you receive an email, where there will be an authentication code. Just copy-paste it. Set up your username and password. And click submit and wait for some time while it initializes and voila!! You are ready to scan!! (you can also learn to install and run nesses on Linux through the link provided at the end of this content!!)
So how do exactly nesses work? Nessus has two different components that make it actually work first we have the client and this refers to that web interface that we actually use as the administrators or users and we can interact with the system the schedule scans generate reports and all kinds of other features the other component is the server component. This is what actually performs those scans and then it sends the results over to the web interface or the client with vulnerability scanning.
Let’s learn some basics about nesses. here are four major steps the first step is port scanning this is where the scanner is going to actually go out there and determine which hosts are alive and which ports are open on those hosts then we have service detection this is where Nessus is going to send out probes to find out which application is running on that port version number. and the actual name of it.
then we have vulnerability identification this is where Nessus is going to compare what it discovers about each service detected on each host and then it’s going to actually compare it against its database of known vulnerabilities of those applications and version numbers and then, finally we have the probing step this is where Nessus is actually going to try to further identify if there are false positives or identify if that vulnerability exists
now, we know some of the basics of vulnerability management and vulnerability scanning.
In conclusion through nesses, you can scan quickly and accurately identify threats, vulnerabilities, and malware.
sites :
to download on Linux – https://docs.tenable.com/nessus/Content/InstallNessusLinux.htm
to download Nessus on mac- https://www.tenable.com/
to learn more about go to :
https://www.tenable.com/products/nessus/nessus-faq
Websites I would personally like to thank you for the making of this content !!
https://docs.tenable.com/nessus/Content/DownloadNessus.htm
https://www.tenable.com/products/nessus/nessus-faq
Also Read : https://thecyberdelta.com/zphisher-2-2-phishing-attack-on-linkedin/
https://thecyberdelta.com/a-i-in-healthcare/








