What is NMAP(Network Mapper)
NMAP(Network Mapper) is developed by ‘Gordon Lyon’.
NMAP (“Network Mapper”) is a free and open source (license) utility for network discovery and security auditing. It uses raw IP packets in novel ways to determine what hosts are are available on the network, what services (application name and version) those host are offering, what operating system (and OS versions) they are running, what type of packet filter and firewall are in use and many other characteristics.
NMAP (Network Mapper runs on all major computer operating systems, and official binary packets are available for Linux, Windows, and Mac OS X. The NMAP (Network Mapper) suite includes and advance GUI and results viewer (Zenmap), a flexible data transfer, redirection, and debugging tool (Ncat), a utility for comparing scan results (Ndiff), and a packet generation and response analysis tool (Nping).
Using the Nmap security scanner
Then you may run the command “nmap” on a terminal, accompanied by the target’s IP or website address and the various available parameters. To get an overview of all the parameters that nmap can be used with, use the “nmap –help” command.

In order to introduce you to nmap, I will give some usage examples together with a brief explanation that will hopefully enable the reader to modify each command to his/her needs.
sudo nmap -sS [IP address] or [website address]This is a basic command that can be used to quickly check if a website is up (in that case, I used the howtoforge.com IP) without creating any “loggable” interaction with the target server. Note that there are four open ports shown as well.

sudo nmap -O --osscan-guess [IP address] or [website address]This command instructs nmap to try to guess what operating system is run on the target system. If all ports are filtered (which is the case in the screenshot), this “guessing” command will be the best option, but the results can’t be considered reliable. The percentage numbers are giving the idea of uncertainty.

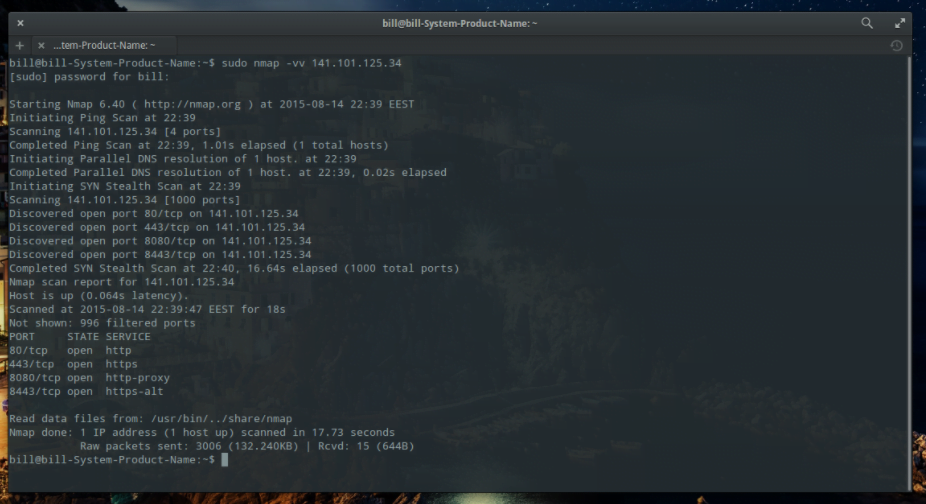
sudo nmap -vv [IP address] or [website address]This is a ping scan command that is helpful when wanting to check the open ports of a target.
sudo nmap -sV [IP address] or [website address]This command allows the user to check the services run on the target. Note that the “cloudflare-ngnix” information was added next to the services of the open ports.

Benefits of NMAP (Network Mapper)
- FLEXIBLE: Supports dozens of advance techniques for mapping out networks filled with IP filters, firewalls, routers and other obstacles.
- POWERFULL: NMAP(Network Mapper) has been used to scan huge networks of literally hundreds of thousands of machine.
- PORTABLE: Most operating systems are supported including Linux, Microsoft Windows, FreeBSD, MAC OS X, NetBSD and many more.
- EASY: Both traditional command line and graphical (GUI) versions are available to suit your preference. Binaries are available for those who do not wish to compile Nmap from source.
- FREE: NMAP is available for free download, and also comes with full source code. The primary goals of the Nmap Project is to help make the Internet a little more secure and to provide administrators/auditors/hackers with an advanced tool for exploring their networks.
- ACCLAMIED: Nmap (Network Mapper) has won numerous awards, including “Information Security Product of the Year” by Linux Journal, Info World and Code talker Digest.
- POPULAR: Thousands of people download Nmap every day, and it is included with many operating systems (Redhat Linux, Debian Linux, Gentoo, FreeBSD, OpenBSD, etc).
What you’ll need
Nmap is a command-line tool that works best on Linux. If you are a Linux user, then you can easily download Nmap(Network Mapper) using your distribution’s package manager (dpkg, rpm, pacman…). It should be available in all Linux repositories, so you won’t have a hard time installing it.
If you have a pen-testing Linux distribution like Kali or Parrot, then Nmap should already be installed with your OS.
For non-Linux users, you can download Nmap here, although I recommend that you switch to Linux if you want to take advantage of all the Linux-based hacking tools.
During this post, we will be performing some of our tests on scanme.nmap.org. This is a test machine maintained by Nmap to help users learn and test their commands legally. You should make sure to not overwhelm this address with scans and only use it a few times a day. Alternatively, you can perform scans on your local network, provided, of course, that you have the proper rights to do so.
The most basic command
Here is the syntax for all Nmap commands :
nmap [options] target
The target can be a domain name, an IP address, a range of IP addresses, or a combination of all these elements.
If you don’t specify options, then Nmap will perform a default port scan of the target.

As you can see, we have obtained some interesting information from the target host by using this simple command:
Nmap does a DNS resolution and provides the IP address of the target.
We know that the host is up.
We have a list of all open ports and their corresponding service.
https://thecyberdelta.com/parameter-tampering/
https://thecyberdelta.com/burp-suite/








clindamycin buy
buy medrol